Set up Microsoft Azure AD as IdP in Keycloak
This page describes how to set up Microsoft Azure AD as an additional identity provider (IdP). This is then offered as an additional button on the login page.
Setting up an application in Microsoft Azure AD
In order for Keycloak to authenticate itself, it must be stored as an application in Azure Active Directory(AD).
Add new application
First, a new "app" must be registered in Azure AD.
-
To do this, navigate to the menu item App registrations
Not to be confused with the item "Enterprise applications". However, this can also be found there later.

-
A descriptive name is then assigned.

-
A secret key must then be generated for the client (keycloak).
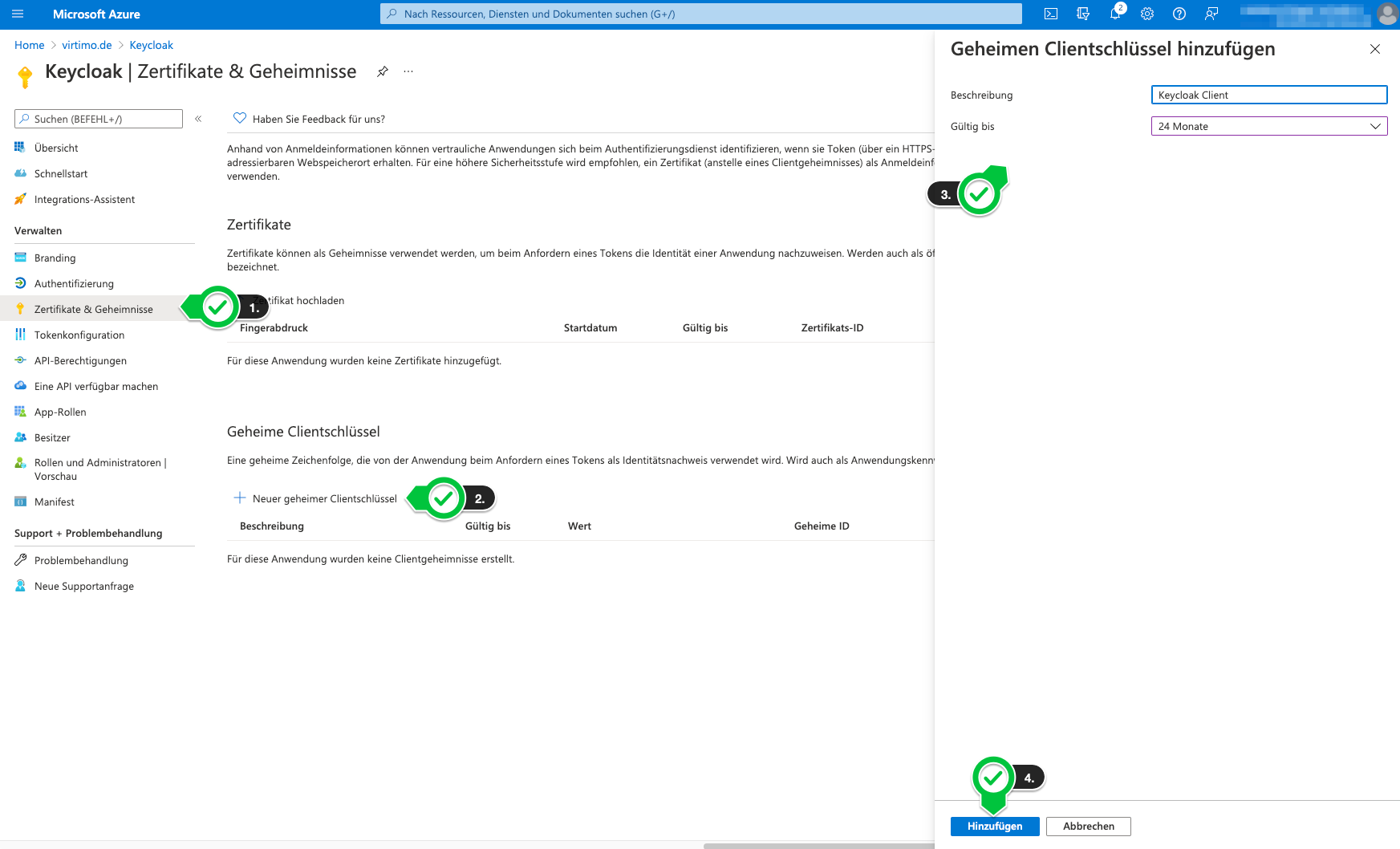
-
The key is displayed immediately after generation and should be saved directly. It is no longer possible to view the key later. If the key is lost, a new one must be generated.
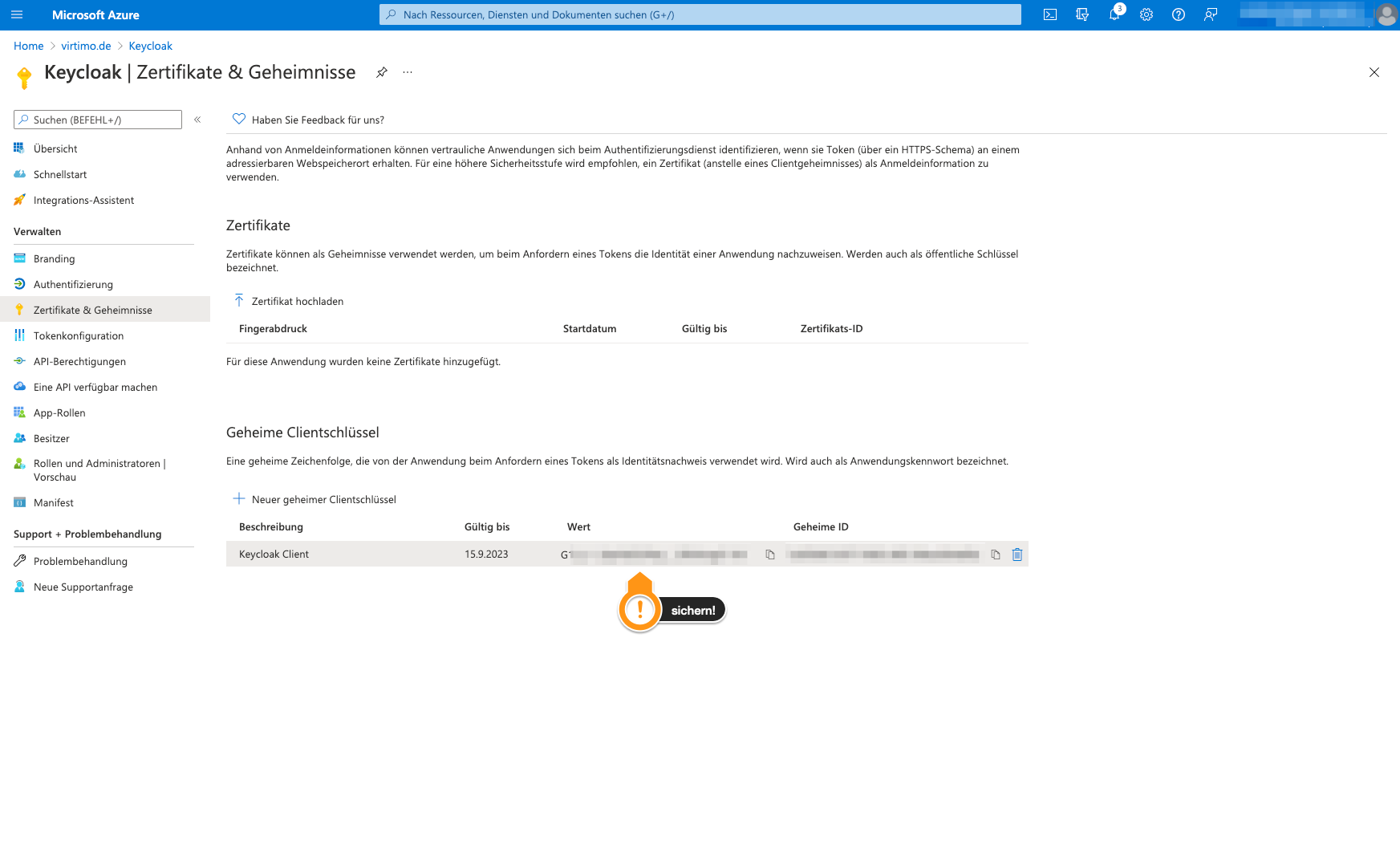
-
The client ID and the URL for the OpenID Connect configuration must then be determined in addition to the secret key.
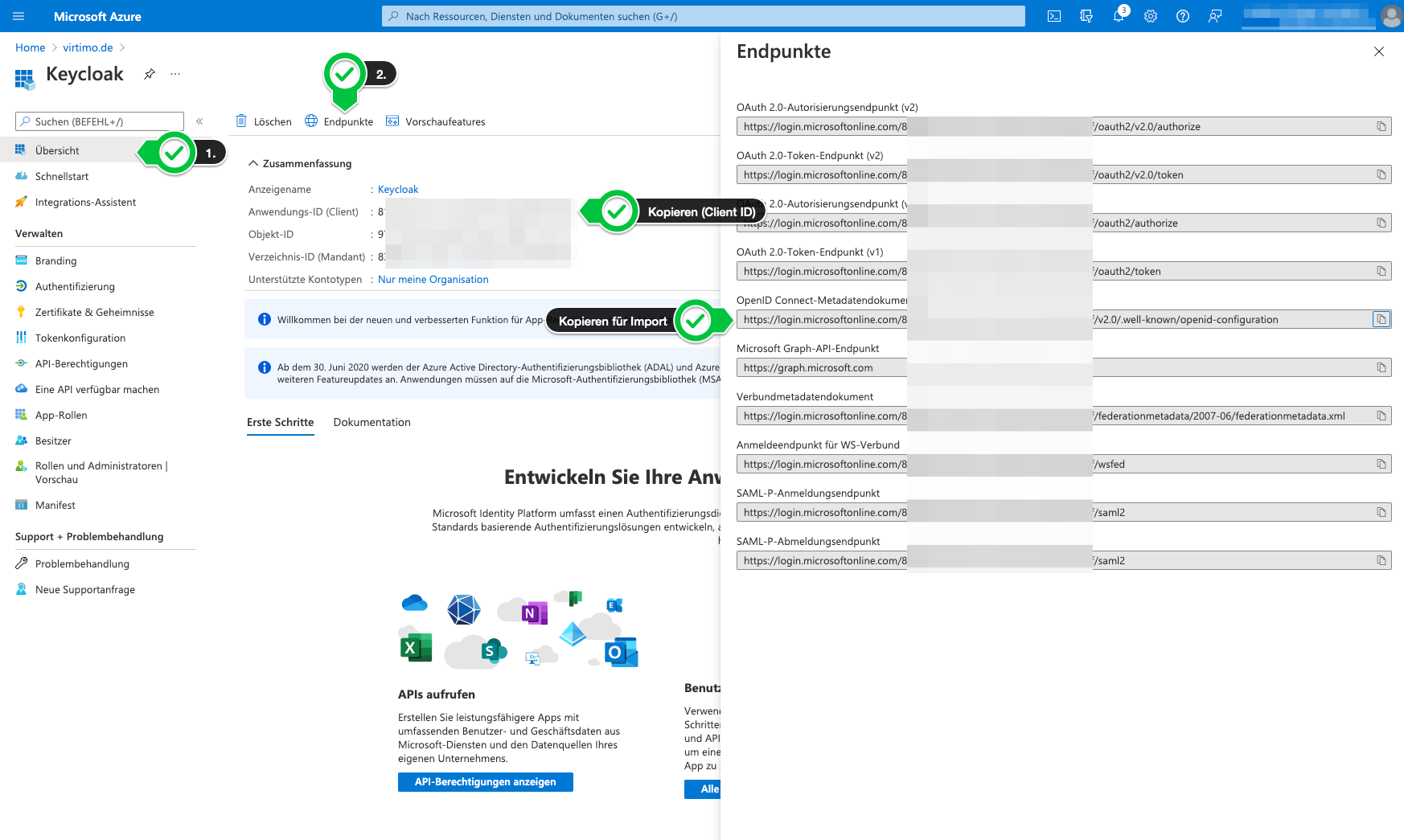
Store IdP in Keycloak
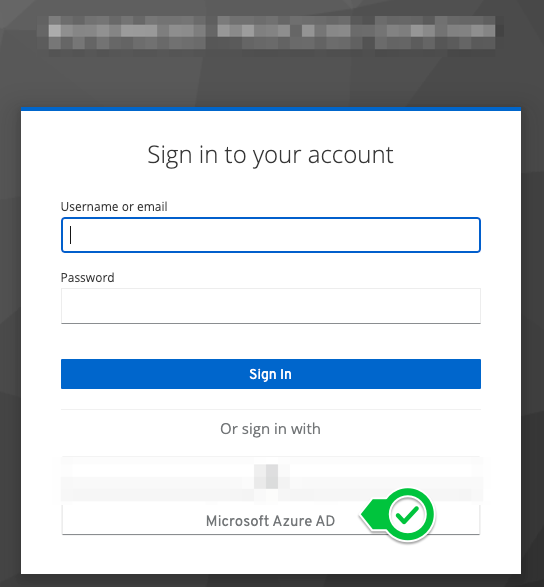
Now you can create a new identity provider in Keycloak.
|
Do not select "Microsoft" under "Social" here. For this option, the client must be configured differently in Azure AD, as in this case login is possible with any Microsoft account (even outside your own organization). |
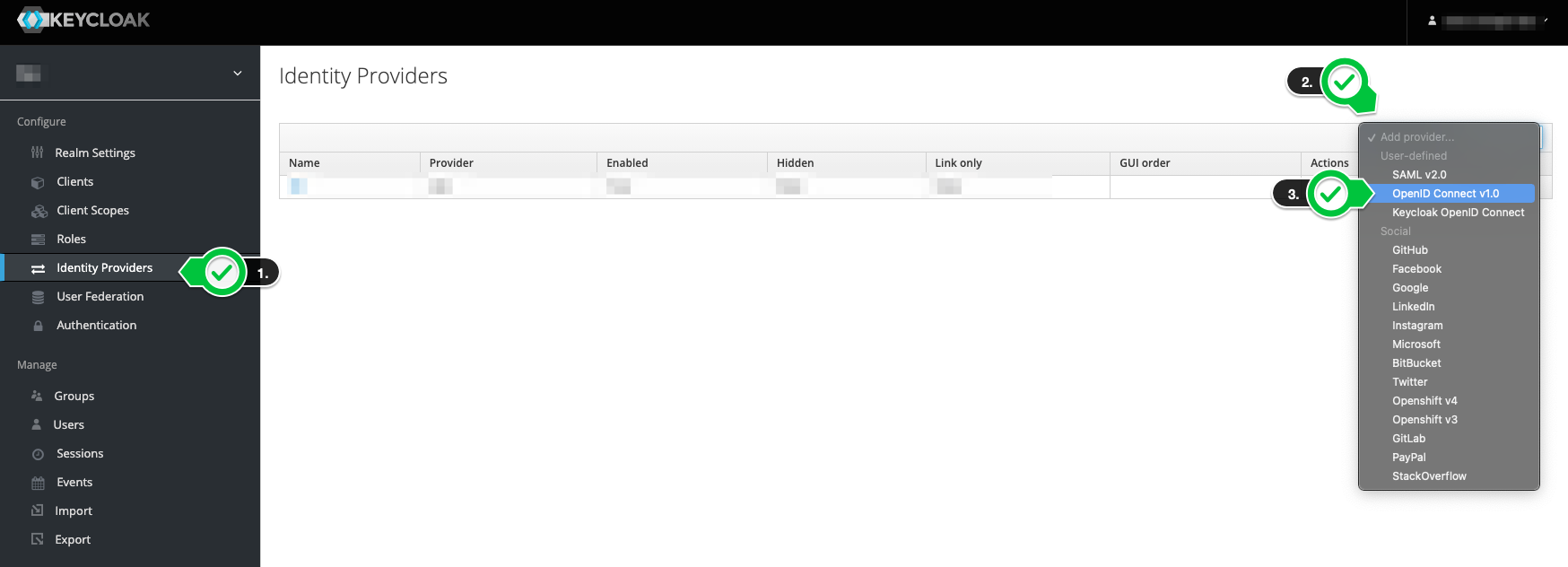
-
In the first step, an alias should be assigned. This has an effect on the redirect URI, which we will need later. The display name determines the name in the login mask of the application.
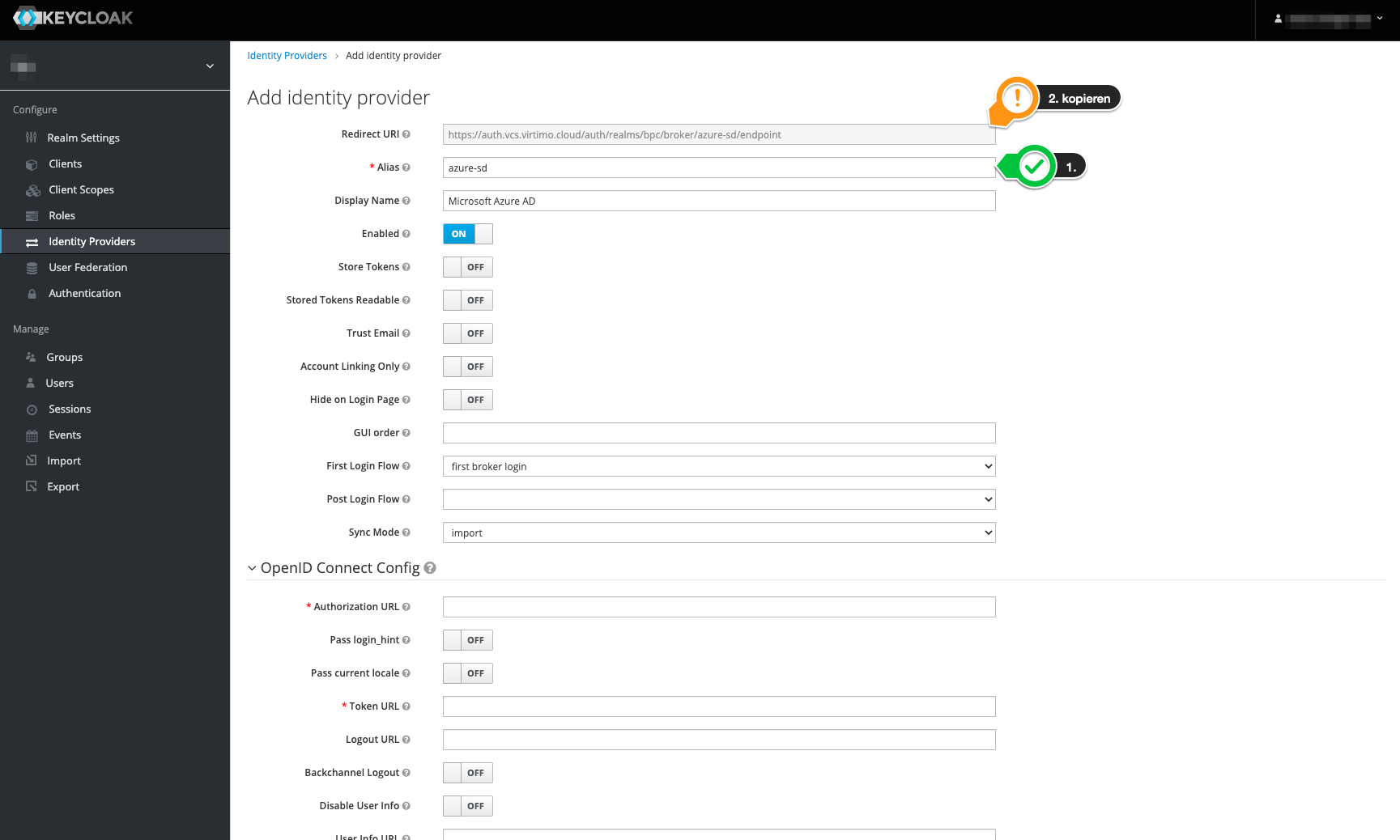
-
Next, the OpenID Connect URL from the Azure AD should be used to configure the endpoints. This must be entered accordingly and loaded using the "Import" button.
All relevant URLs are then filled in automatically.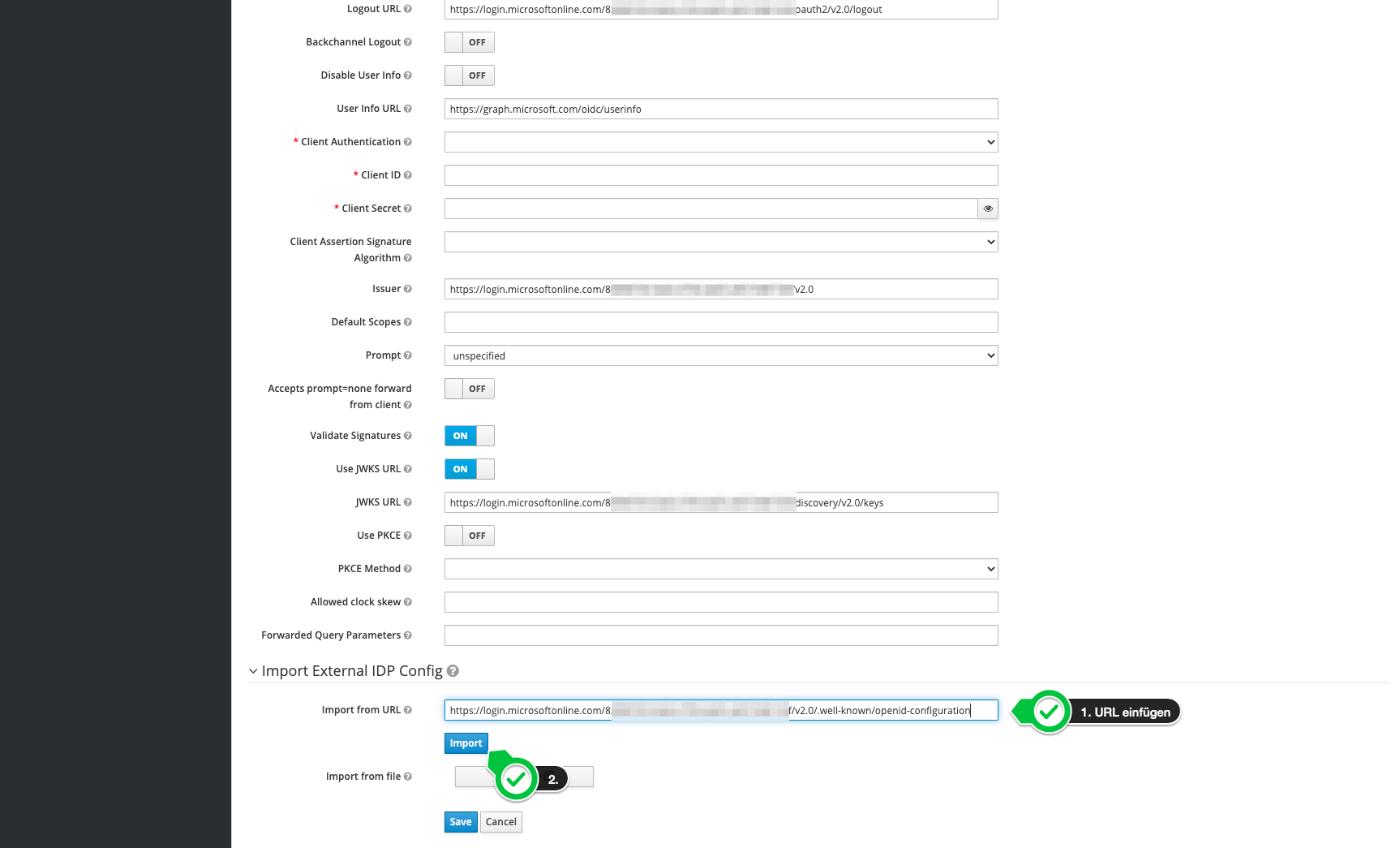
-
Finally, the client ID and the secret key must be entered.
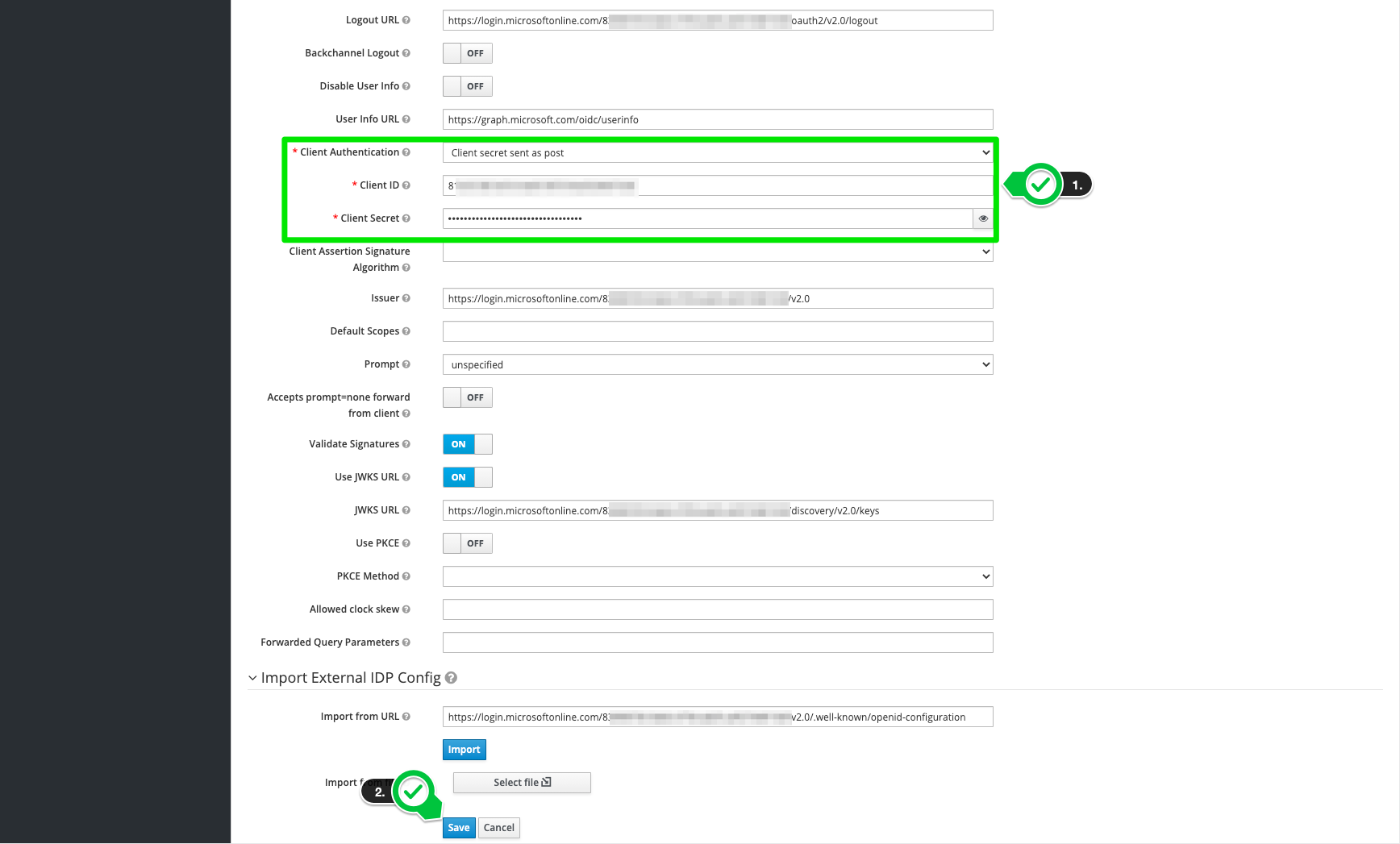
-
The redirect URI from the previous step must now be stored in the Azure AD.

Troubleshooting
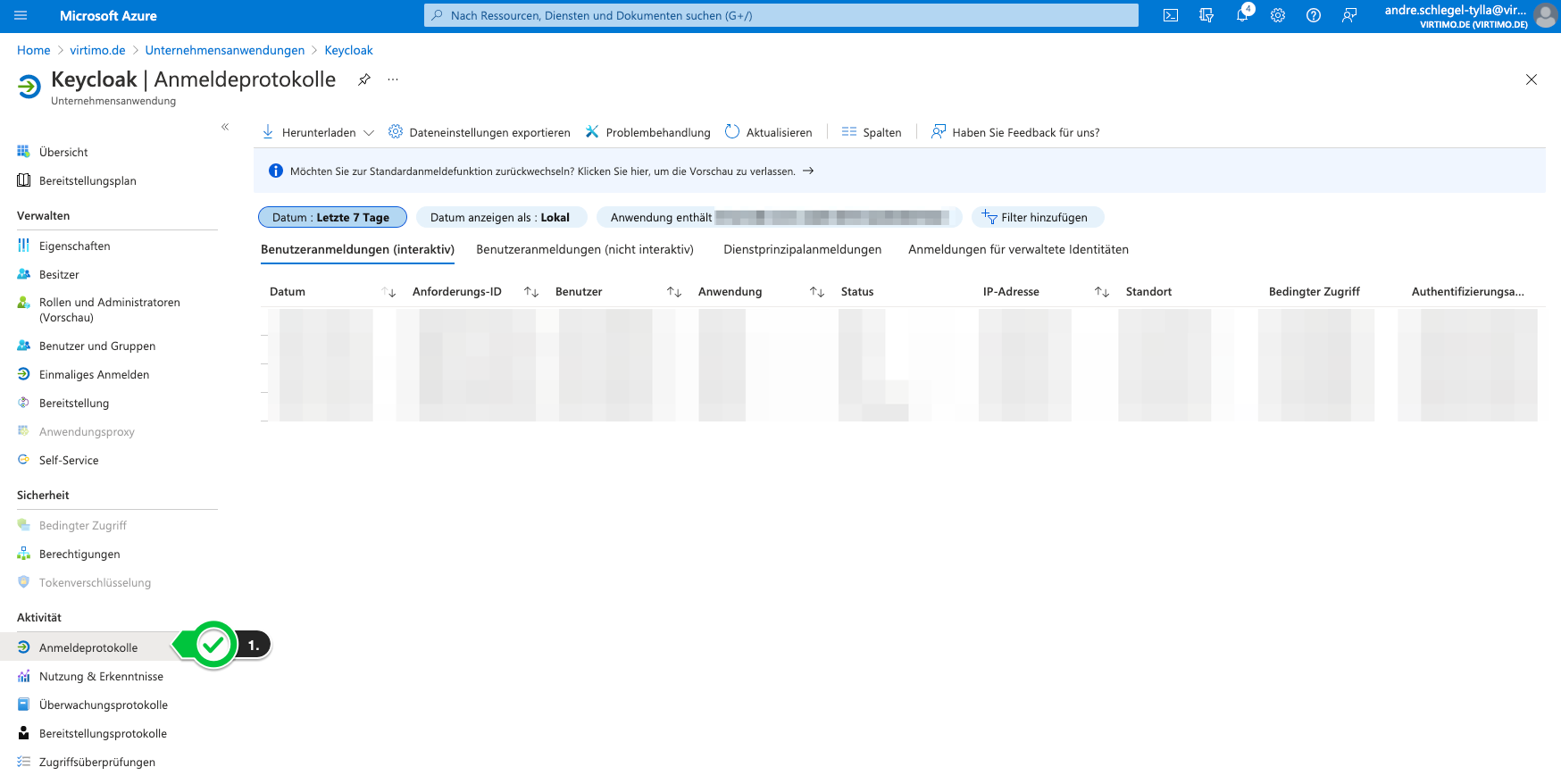
It is not so easy to find errors in this setup. One source can be the logs in Keycloak. In case of doubt, however, it is up to you to decide what is wrong on the Azure AD side. To see incorrect logins, you have to navigate through the interface as follows.
-
Open company applications in Azure AD.
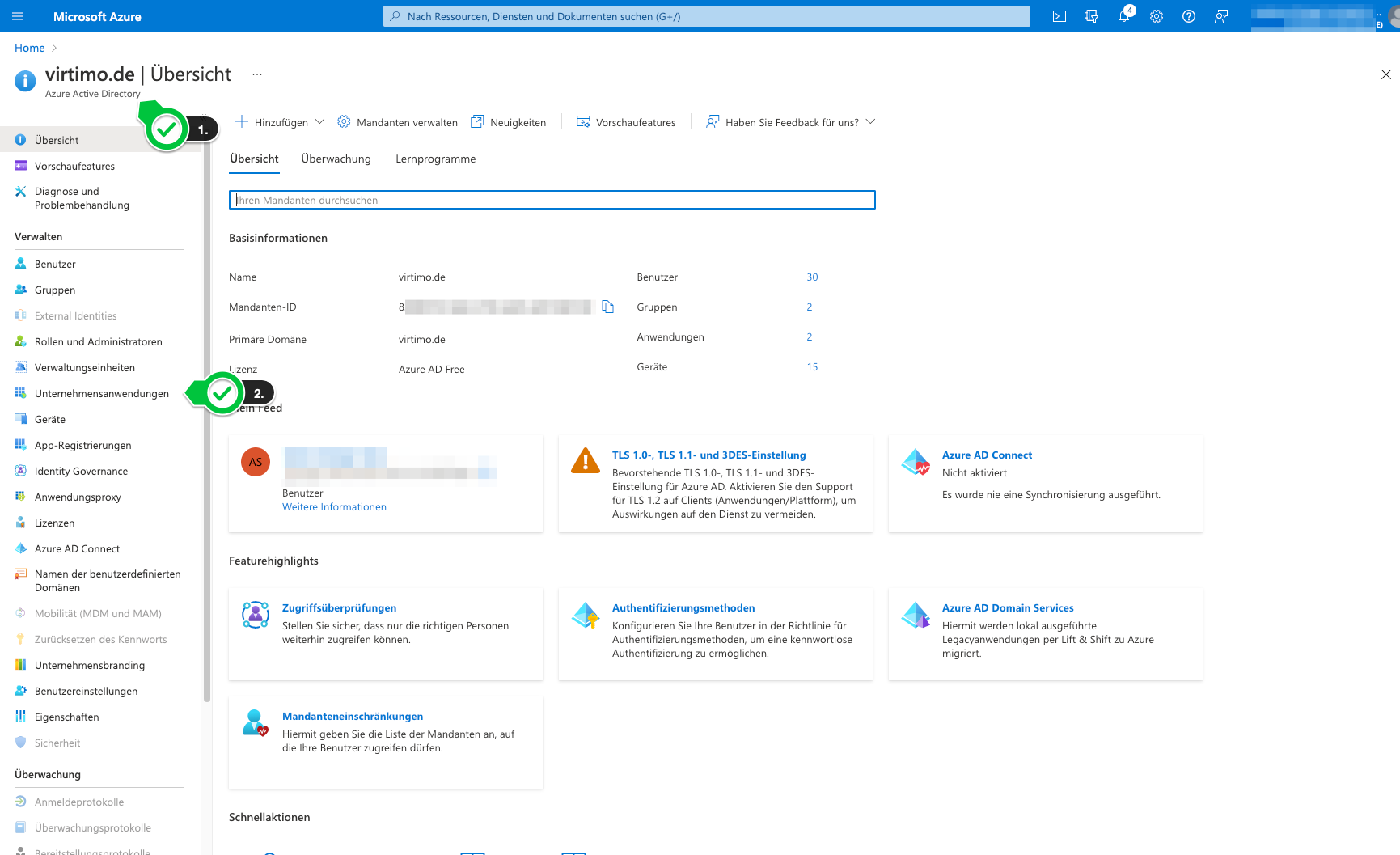
-
Select your own application/APP.
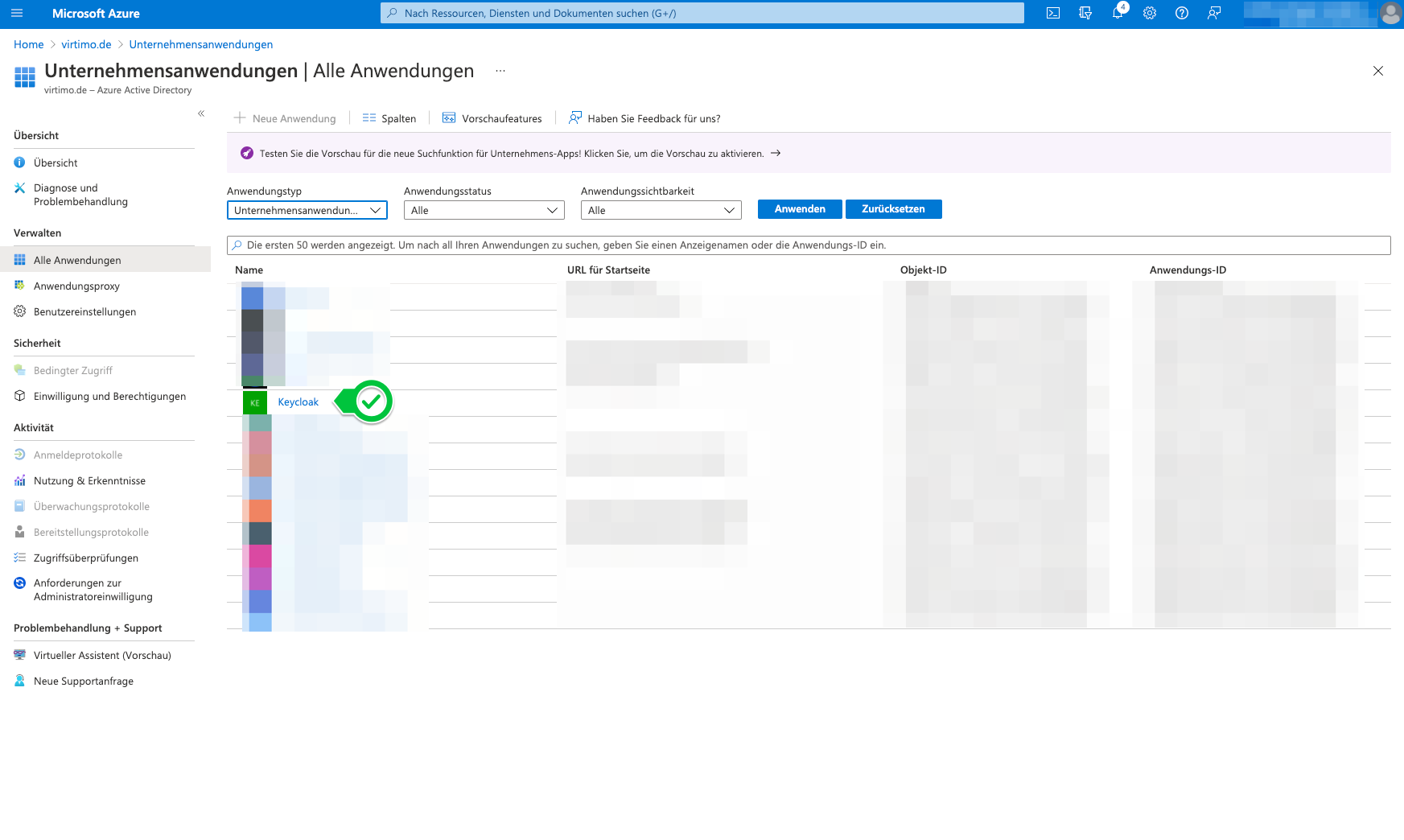
-
Open logon logs.