Connecting and Configuring Process Users and Roles
You can use process users from an external user administration, e.g. you can connect to an LDAP directory service.
The users and roles used in the processes are determined dynamically at runtime from LDAP.
Concept
Connecting to an external user administration offers the possibility of controlling e.g. INUBIT tasks through an external client and external management of process users. The complete authentication and authorization (for example, tasks only for certain roles) is handled through the configured server connection.
Process users
Process users are process participants who use processes configured in the INUBIT software or are used in it (e.g. as customer data) and are connected through the portal (e.g. BPC) or another user administration (e.g. LDAP). Accordingly, there are process user roles that classify the process users into certain rights containers. In this way tasks can be created for specific roles and thus made available to certain users who are assigned to these roles.
Process Engine users
Process Engine users are technical users within INUBIT Workbench that log on to the Workbench as users and configure workflows, for example.
Prerequisites
-
You have the technical parameters of the server to be connected.
-
You have access as an administrator user to INUBIT Process Engine or INUBIT Workbench.
Connecting Process Users and Roles from LDAP Server
To use external user administration for the INUBIT process users, e.g. for managing tasks, you can connect an LDAP directory service.
Features
-
The users and roles used in the processes are determined dynamically at runtime from LDAP.
-
The process users and roles present in the INUBIT software can be queried from LDAP without portal use.
-
The INUBIT task mechanism operates via LDAP rather than through the portal. In this way the INUBIT REST interface directly supports authentication against the LDAP connection of the INUBIT Process Engine configured in the Workbench.
Prerequisites
-
You have the technical parameters of the LDAP server to be connected.
-
You have access as an administrator user to INUBIT Process Engine or INUBIT Workbench.
Configuring the Connection to the LDAP Server
You configure the connection to the LDAP server in the corresponding dialog in INUBIT Workbench.
Proceed as follows
-
Display the Administration > General Settings tab in the INUBIT Workbench.
-
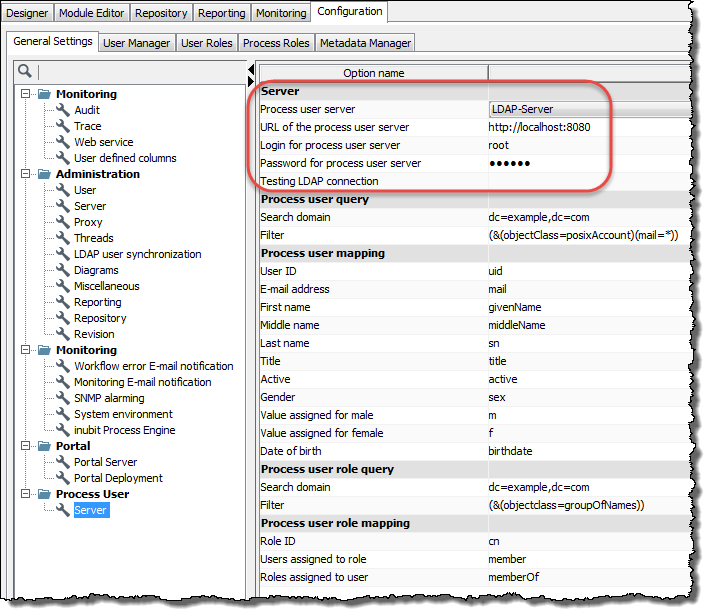
Open the Process User > Server configuration area.
-
In the Server area, enter values valid for your system for all options:
Option Explanation Process user server
For selection and activation of the server (the LDAP server in this case) from which the process users are to be connected and queried.
URL of the process user server
IP address/host or URL of your LDAP server, such as
ldap://10.8.209.98.Login for process user server
Login parameters for authentication with the LDAP server,
BindDNthe LDAP basic node, e.g.cn=Manager, dc=team1, dc=dePassword for process user server
Access password of your LDAP server
Testing LDAP connection
For testing whether the connection to the LDAP server can be established successfully with the information you entered.
Configuring Multitenancy
To query users and/or roles from a specific tenant from an external user directory with tenant configuration, multitenancy must be activated and configured.
For LDAP
Such a structure of tenant representation in the LDAP directory is assumed by way of example:
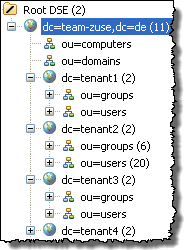
The tenants shown as tenant<No.> are all located on a level below the LDAP basic node.
Each tenant node contains all users and roles valid for this tenant.
Activating multitenancy
Proceed as follows
-
To activate the multitenancy function, open the tab Administration > General Settings in the Workbench and navigate to Administration > Server.
-
Select the Multitenancy for tasks option. In this way, multitenancy is enabled for the connection to the external directory.
Note that activation of this option also defines that tasks are always created for a specific tenant. This automatically corresponds to the user group in INUBIT Process Engine or Workbench.
-
Adjust the search domains.
To enable searching for objects of a tenant in the LDAP directory, the search domain in the LDAP configuration must be adjusted under General Settings > Process User > Server:
-
In
-
the Process user query area and
-
the Process user role query area, set the placeholder
$CLIENTin the Search domain field.For the Process user query area, that would be
ou=users,dc=$CLIENT,dc=team-zuse,dc=de, for example.With a REST query of a process user / a process user role of a tenant, your query must contain the attribute
&client=<tenantId>. ThetenantIdspecified here then replaces the placeholder$CLIENTin the search domain. The placeholder$CLIENTthus ensures that the query of the LDAP node relates to the associated tenant.
-
-
Configuring LDAP Queries
To be able to query process users and process user roles from an LDAP directory via REST interface, for example, you must configure the corresponding queries in INUBIT Workbench.
Depending on the search domain and filter, the LDAP query returns specific objects from the LDAP directory tree on a targeted basis.
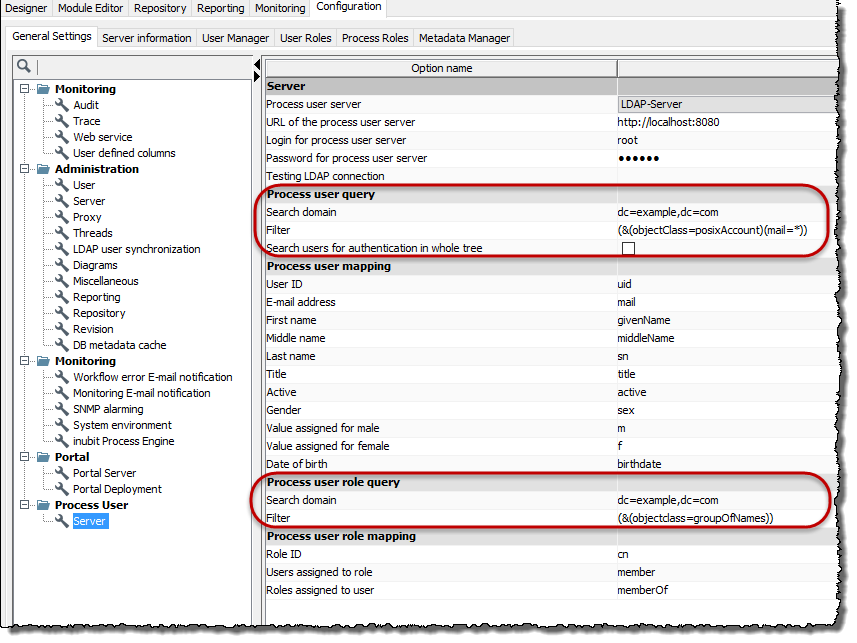
The query configuration is done separately for process users and process user roles in Administration > General Settings > Process User > Server:
Proceed as follows
-
Display the Administration > General Settings tab in the INUBIT Workbench.
-
Display the Process User > Server area.
-
Depending on whether you want to configure a query for process users or process user roles, select the corresponding area:
-
Query for process user or
-
Query for process user roles
-
-
For the options Search domain and Filter, enter the required values:
| Option | Explanation | ||
|---|---|---|---|
Search domain |
The Example
Defines the object |
||
Filter |
Enter your required filter. The filter is applied to all LDAP objects beneath the search domain, and all objects that match the filter criteria are returned. Example
This filter returns all users that correspond to the objects in the default LDAP directories of the object class |
||
Search users for authentication in whole tree |
If activated, users with the matching user id are identified in the tree and all its subtrees while authenticating.
|
|
If you have activated multitenancy, you need to set the placeholder |
Configuring Attribute Mapping
The individual objects in the LDAP directory and the process users in the INUBIT software each have attributes that need to be correctly mapped to each other. This is the only way that objects can be searched for and output.
To map the process users of the INUBIT software to the attributes of the LDAP objects or process users and roles, you need to configure mapping – separately for users and roles – in the LDAP configuration dialog of the Workbench.
Proceed as follows
-
In INUBIT Workbench, display the Administration > General Settings tab and the Process User > Server area.
-
Choose whether you want to perform the mapping for process users or process user roles or for both categories in succession:
-
Mapping users
-
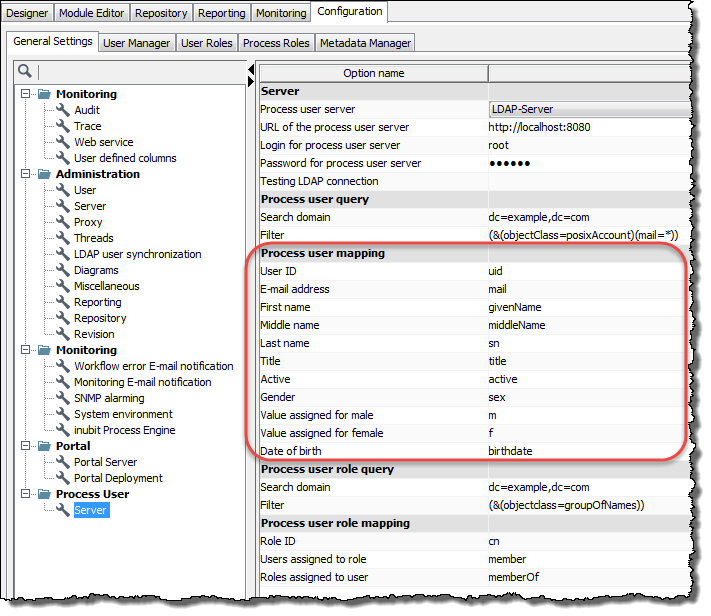
Select the area Process user mapping:
-
Enter the appropriate values of your LDAP system for all INUBIT attributes listed in the
Option namecolumn:Option Required Data type E.g. in openldap User ID
Yes
String
cn (top)
E-mail address
Yes
String
mail (inetOrgPerson)
First name
Yes
String
givenName (person)
Middle name
No
String
displayName (person)
Last name
Yes
String
sm (person)
Title
No
String
title (organizationalPerson)
Active (account active)
No
Boolean
active
Gender
No
String
gender
Value assigned for male
No (only if
Genderis set)String or integer
0
Value assigned for female
No (only if
Genderis set)String or integer
1
Date of birth
No
LDAP date
birthDate
-
-
Mapping roles
-
Select the area Process user role mapping:
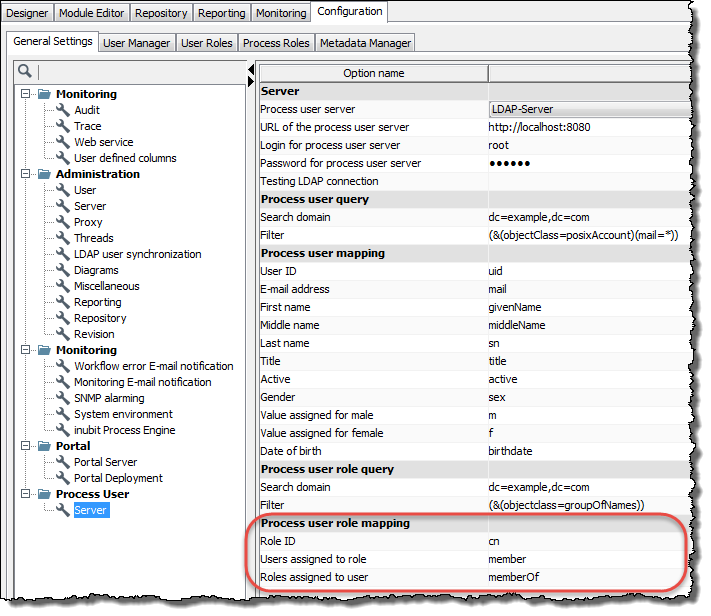
-
Enter the appropriate values of your LDAP system for all INUBIT attributes listed under
Option name:Option Required Data type E.g. in openldapRole ID
Yes
String
cn
Users assigned to role
Yes
String
member
Role assigned to user
Yes
String
memberOf
-
-
Testing the Connection to the LDAP Server
To test whether the connection to the LDAP server and the configuration of the LDAP queries and of the attribute mappings were successful, you can perform a connection test
Prerequisites
-
The connection to the LDAP server has been configured:
-
The LDAP queries have been configured.
-
The attribute mapping has been configured:
Proceed as follows
-
Display the dialog for LDAP configuration in Administration > General Settings > Process User > Server.
-
In the Server area, click the Open button next to the Testing LDAP connection option.
The Testing LDAP connection dialog opens and displays the test results, separated according to users and roles, or the prompt for entering the required tenant.
Without multitenancy
-
If multitenancy is not activated, the configured search query and the attribute mapping are automatically checked after the connection test is called up.
After successful testing, the configured mapping and the corresponding values ??for the first hits based on the search query will be displayed, e.g.:
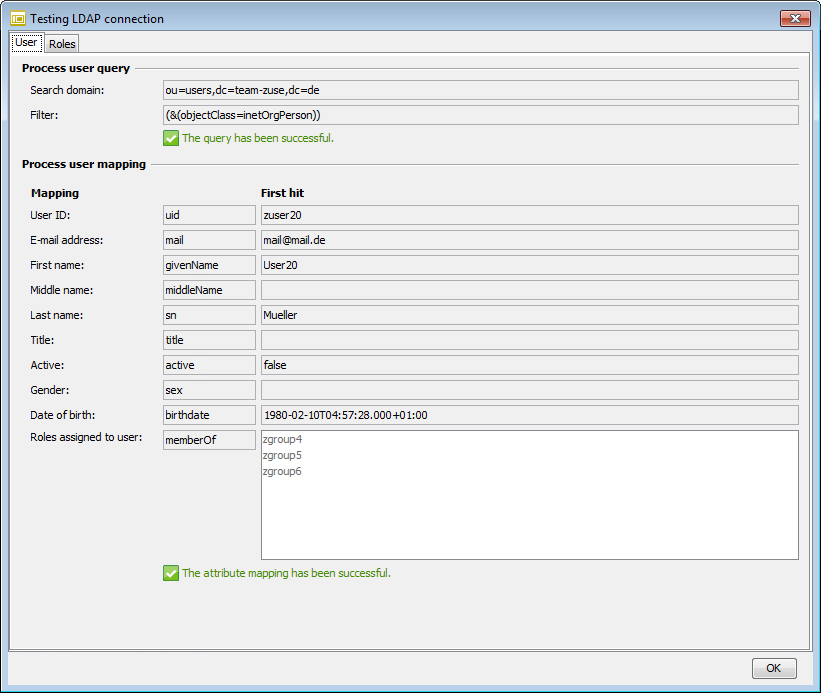
If the filter in the top dialog area is incorrect, the entire lower area is hidden and a corresponding error message is displayed.
If the attribute mapping is incorrect, an error message is displayed below the mapping.
When you change to the Roles tab, the connection test is automatically performed also for the role mapping and displayed like the results for users.
With multitenancy
-
When multitenancy is activated, you must first enter the required tenant in the test dialog and then trigger the actual connection test by clicking the Test button. The first hit based on the search query for the tenant is displayed, e.g.:
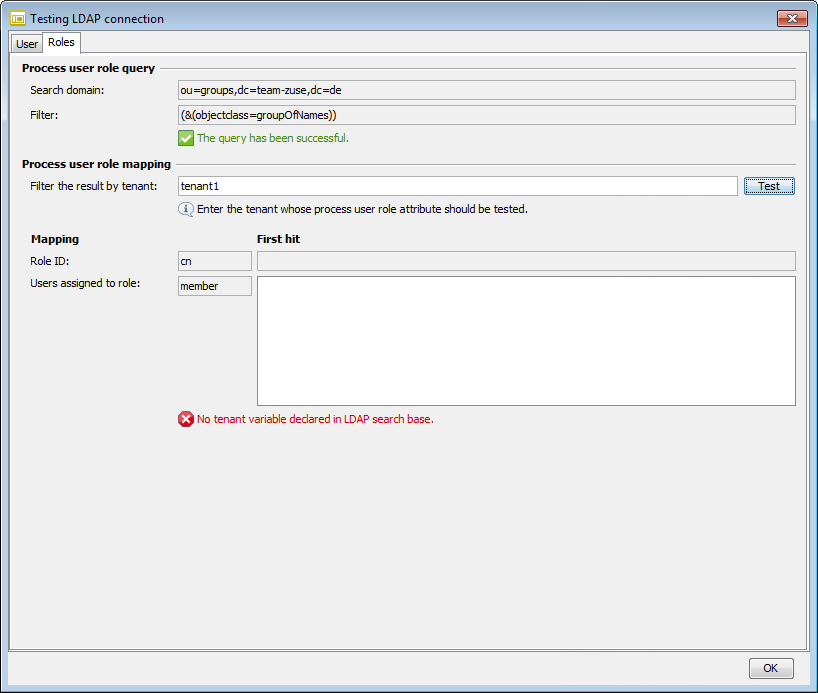
Querying Process Users and Roles from LDAP
After the necessary configurations (queries and attribute mappings), you can use the REST interface of the INUBIT software to use users and roles from LDAP for the following functions:
User
-
Obtain process users from LDAP based on their names in order to use them for task management, for example.
Roles
-
Obtain process user roles from LDAP in order to be able to use all roles from LDAP for selecting the process user roles when creating a new task generator, for example.
User-role combination
-
Obtain process users for certain roles from LDAP in order to only display tasks for users with this role, for example.
Task list
-
For all queries of the task list via REST, LDAP is used for authorization and authentication
|
When multitenancy is activated, you need to set the
|
For detailed information about the REST-based interface of the INUBIT software, refer to REST API.
