Imitating users with Keycloak
This feature allows an authorized user to impersonate another user. This is known as impersonating or impersonating users.
Use
In the integrated user administration, impersonation can be triggered via the button on the respective user. This immediately logs you in as this user.
Alternatively, this can also be activated from the user administration in Keycloak.
Keycloak configuration
In order for the impersonation to be carried out, adjustments must be made in the Keycloak and in the BPC.
Activation of the necessary feature
The so-called Token Exchange Service feature (ID: token-exchange) must be activated.
Otherwise the error Feature not enabled will occur.
If you want to prevent the impersonation of certain users (see Restrict impersonation), you must also activate the Fine-Grained Admin Permissions feature (ID: admin-fine-grained-authz).
You can find out how to activate the feature in the Keycloak documentation.
Permissions
The necessary permissions for this function can be found under Keycloak permissions.
Enable impersonation detection
In order for the BPC to recognize that a user is impersonating another user, the transfer of this information must be set up.
To do this, add suitable mappers to one of the client scopes used (e.g. ). profile
Under Mappers these can be added via Add mapper → From predefined mappers.
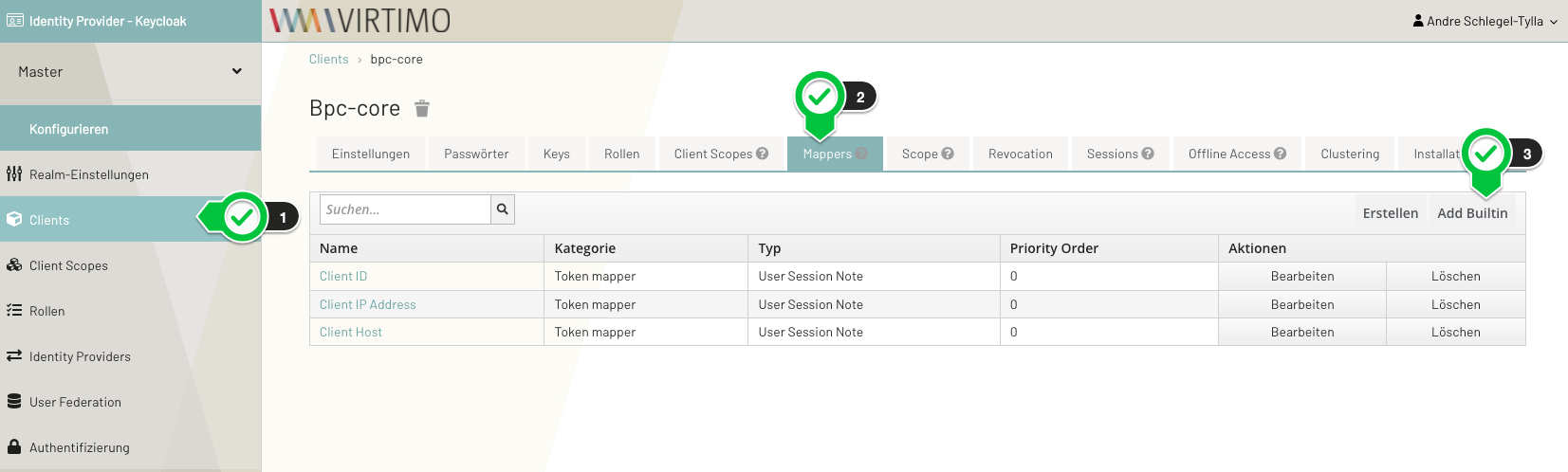
The following mappers must be added:
-
Impersonator Username
-
Impersonator User ID
If these mappers are set, information about who is imitating the current user is stored in the user session.
|
If this is not configured, the BPC cannot recognize that a user is being impersonated. This would result in the BPC audit log not recognizing that a user has been impersonated. |
Restrict impersonation
Please note that users who impersonate other users also receive their authorizations. This may result in an unintentional extension of rights.
To prevent this, you can influence who is allowed to impersonate whom in the keycloak. To do this, the corresponding feature (see Activation of the necessary feature) must be activated. Then proceed as follows in the Keycloak:
-
Create a role.
-
Create a client policy of type
Roleat the clientrealm-management-
Add the role created first to the policy and activate the checkbox
Required field -
The setting at
Logicis decisive.-
Positive- Members of this role can be impersonated, users without this role cannot -
Negative- Members of this role cannot be impersonated, users without this role can
-
-
Activate in the user list
Permissions -
Select from the list
user-impersonated -
Select the previously created policy in the permission and save the changes
-
See also the Keycloak documentation.
BPC authorizations
The required authorizations are described on the User administration / Identity Manager page.
