Create, configure and use an identity provider
The BPC requires the connection of an external identity provider (IdP). The BPC offers corresponding settings in the administration area for the configuration of the external IdP. An Identity Provider is created in the BPC under Backend Connections and then defined as the Identity Provider to be used in the Core Services settings.
When the BPC is started, an Identity Provider Backend Connection is created for the local Karaf with the ID idp_karaf and the name Karaf (default).
This is also immediately used as the active Identity Provider.
It is recommended to use Keycloakfootnote:[Keycloak is a trademark of The Linux Foundation] as the identity provider. Keycloak is open source and implements standards such as OpenID Connect and SAML. This can also be used to map very complex scenarios.
Creating and configuring identity providers
Identity providers are generally configured via backend Connections.
General identity provider configuration
The following configuration parameters can be found at Backend Connections of type identity_provider.
Settings for the AdditionalInfo group are described at Add additional organizations/roles/rights and other data to the user session.
| Setting (Key) | Group | Type | Description |
|---|---|---|---|
IdentityProvider |
Config |
text/combobox |
Identity Provider Service. Default: |
IdentityProvider_URL Only BPC version < 4.2.13 |
Config |
text |
The URL at which the identity provider can be reached |
IdentityProvider_Configuration Only BPC version < 4.2.13 |
Config |
json |
Configuration Object for Identity Provider |
Config |
json |
Mapping of the role between BPC and Identity Provider. |
|
IdentityProvider_HealthEndpoint |
Config |
text |
Health endpoint of the identity provider. If set, the status of the identity provider can be queried via the status API. |
Config |
text |
The URL at which the Self Service can be reached |
|
IdentityProvider_PasswordValidationRegExp |
Config |
text |
Regular Expression(see Java documentation) for validating passwords. For example, for Complex example consisting of several parts:
|
IdentityProvider_ChangeOrganizationEnabled |
Frontend |
bool |
Enables the deactivation/activation of the change of organization in the interface. |
IdentityProvider_ChangePasswordEnabled |
Frontend |
bool |
Enables the deactivation/activation of the change of password in the interface. |
Use Identity Provider
One of the Identity Providers created above can now be defined in the Core Services → Settings as the (Active) IdP to be used. If it is then not possible to log in with this IdP, you will find a solution at Forcing the local IdP as a fallback
| Setting (Key) | Group | Type | Description |
|---|---|---|---|
IdentityProvider_BackendConnection |
identityProvider |
text/combobox |
Select/set the Identity Provider Backend Connection to be used. |
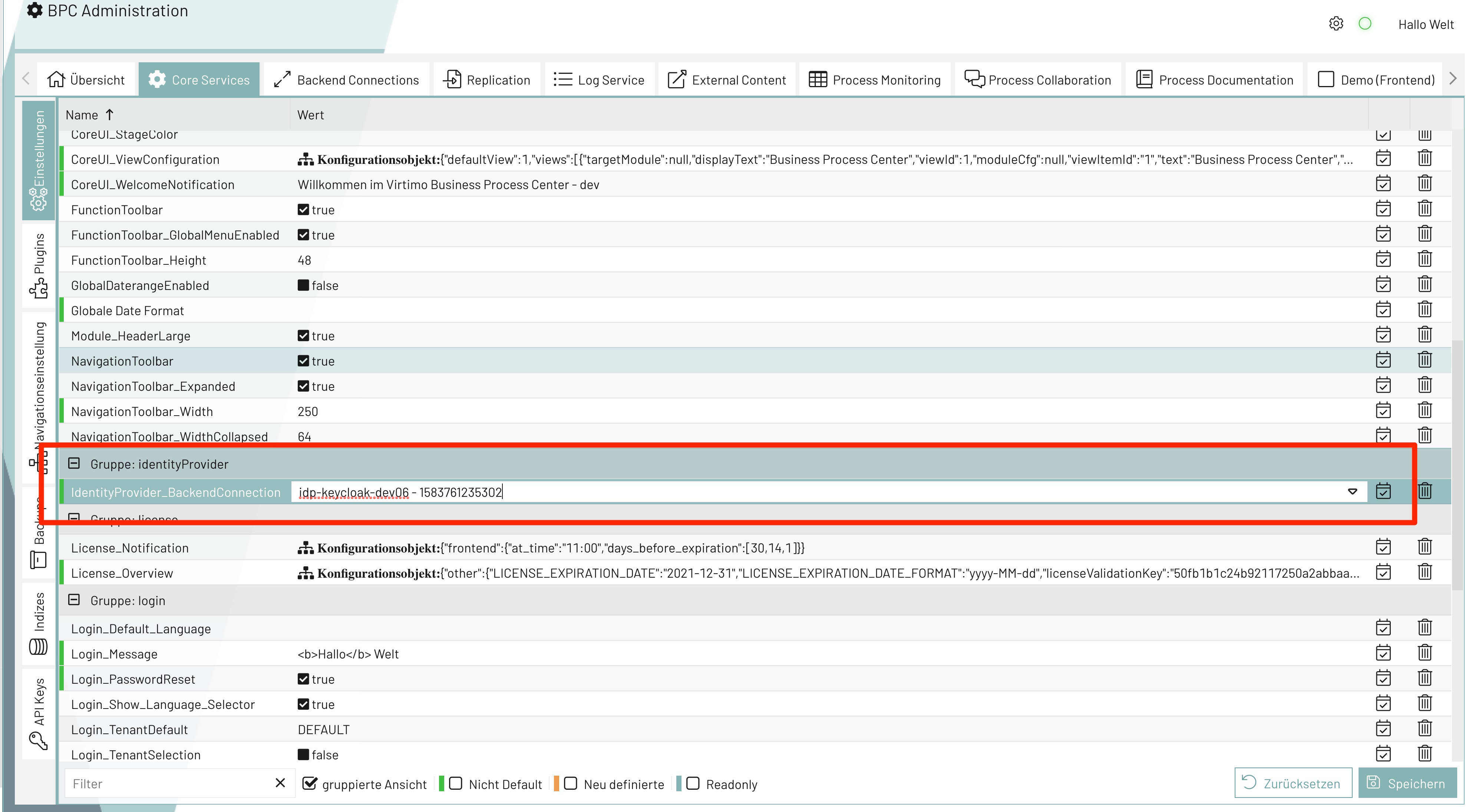
Click on "Save"!
You will then be logged out and must log in again.
The new identity provider will be taken into account.
