Management
The management view is accessed via the global menu and allows you to set global settings and configure centrally usable functions.
Global settings
The number of threads and the time zone used for the application can be adjusted under the general settings.
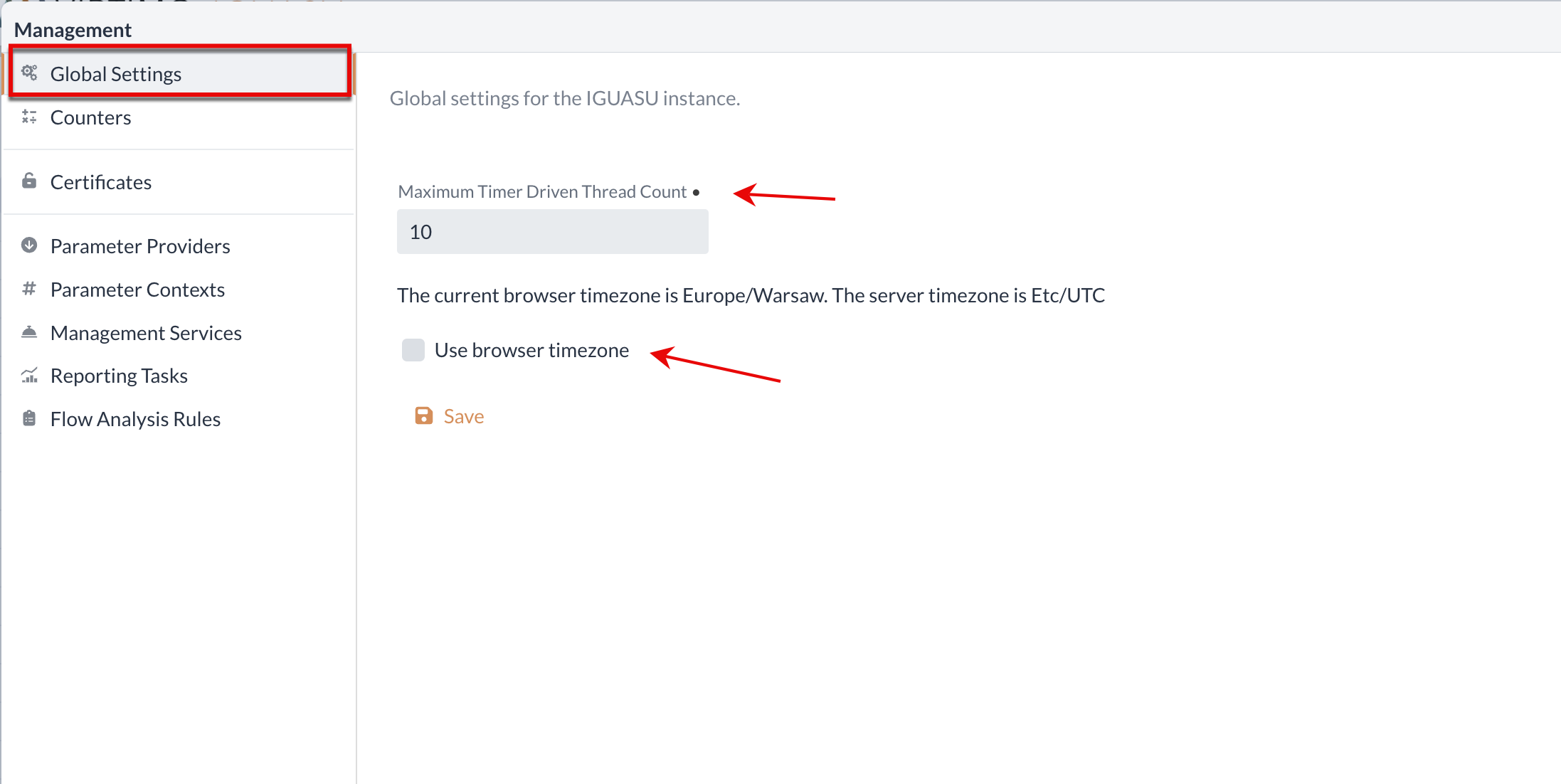
The setting option Maximum Timer Driven Thread Count specifies the maximum number globally for all Processors, which is then distributed to the Processors.
If only one thread is allowed globally and two Processors only have one thread individually, then they must wait for each other.
If a thread has been set on a Processor and the Processor takes a very long time to execute, e.g. for an SQL query, the thread is not executed.If a thread is set on a Processor and the Processor takes a very long time to execute, e.g. for an SQL query, then this Processor is not available for another FlowFile during this time.
Typically, it makes no sense to configure the number of threads on a Processor to be far above 10. You should start with one thread and adjust the number if a bottleneck forms on this Processor (i.e, flowFiles accumulate in the queue in front of it).
If you have I/O-heavy flows, it may make sense to set Maximum Timer Driven Thread Count to a higher value than the available cores of the Processors.
In such a case, the threads wait a long time for I/O and other threads from the pool can be executed.
From a certain point, however, the context switch costs too much and additional threads have a negative effect.
|
As a guideline, 2 to 4 times the available processor cores should be available as threads, thus achieving a good base value. |
This section also provides the option of defining the time zone based on the browser. For this purpose, the checkbox in the menu can be used, whereby the current time zone of the browser is automatically adopted.
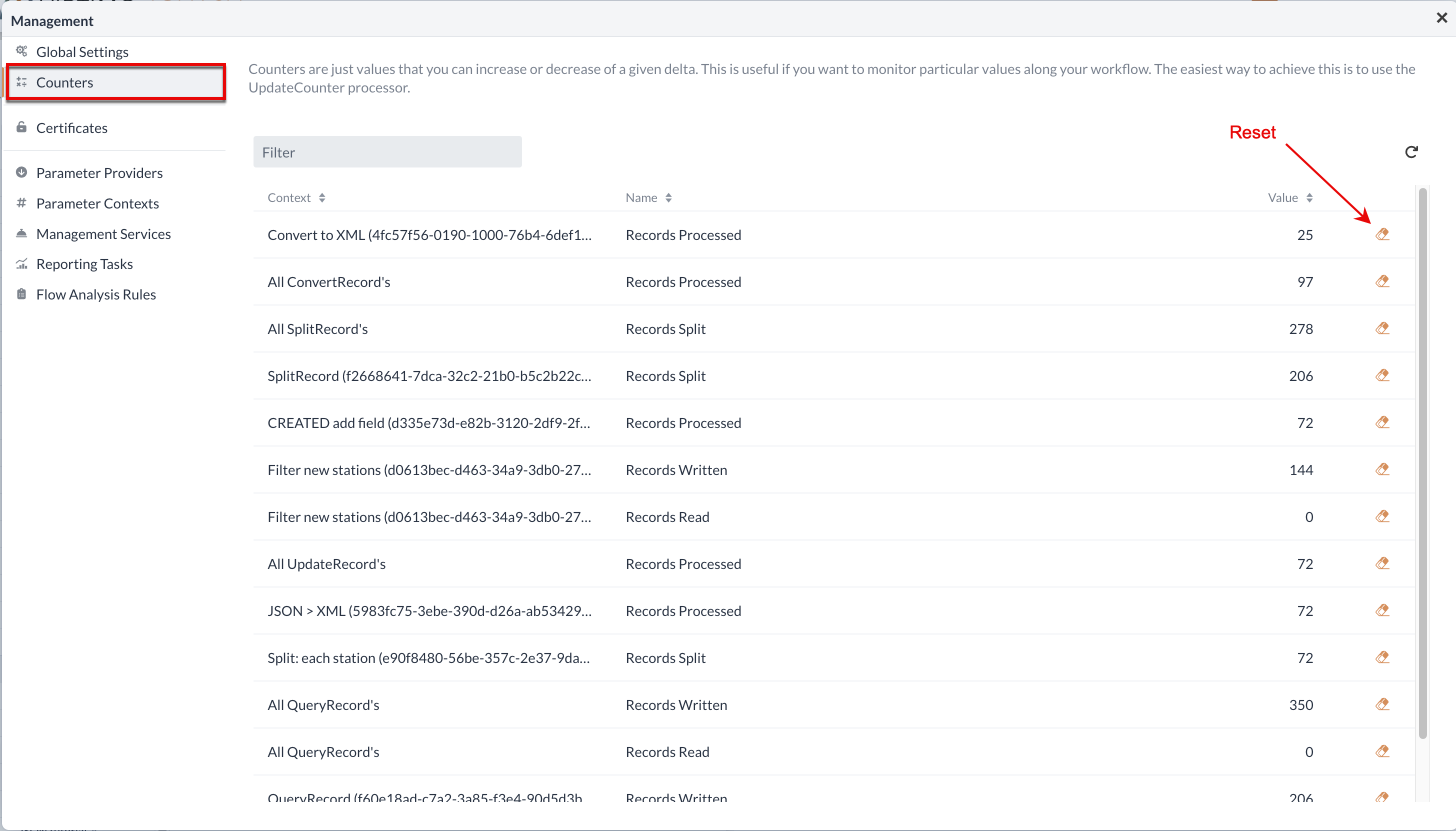
Counters
Counters are values with which certain delta can be increased or decreased. This is useful if certain values in your workflow are to be monitored. The easiest way to achieve this is to use the UpdateCounter Processors.
Certificates
General
In the application’s certificate manager, the existing certificates can be edited and customized to enable secure communication to other applications.
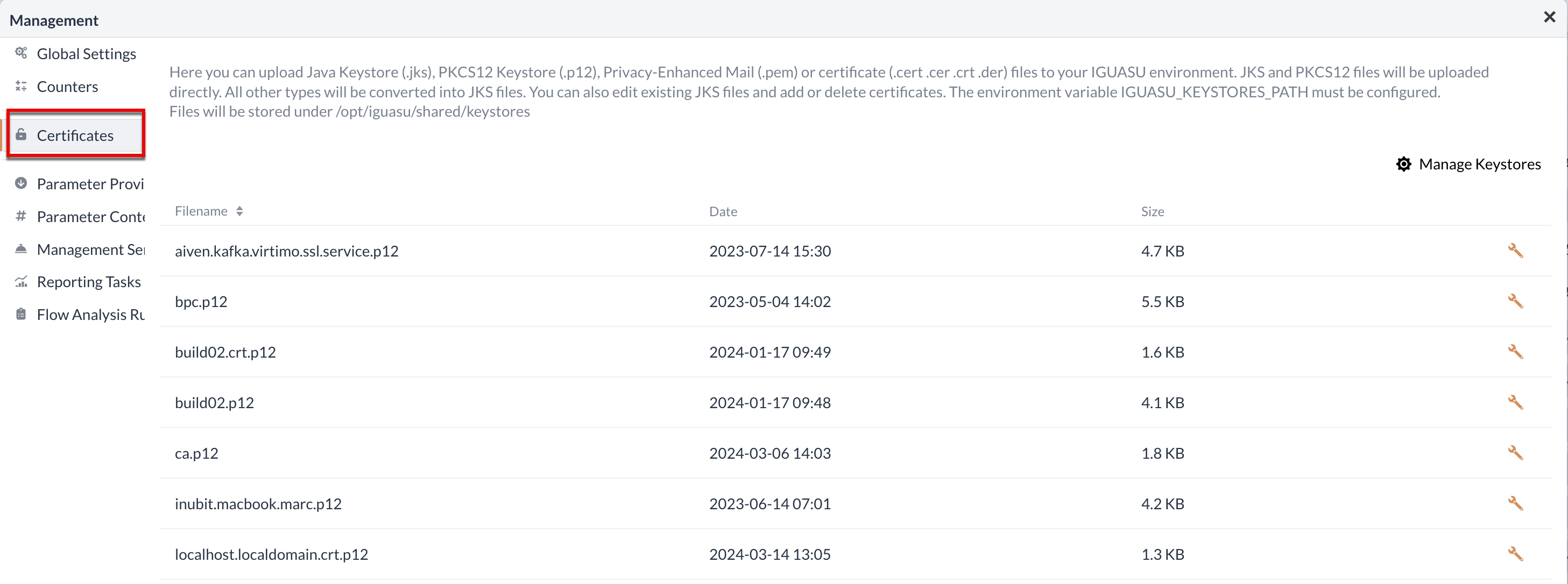
In this area, various options are available for generating a keystore or certificates.
Keystores can be generated, uploaded, imported or exported by interacting with the Add Keystore button above the table.
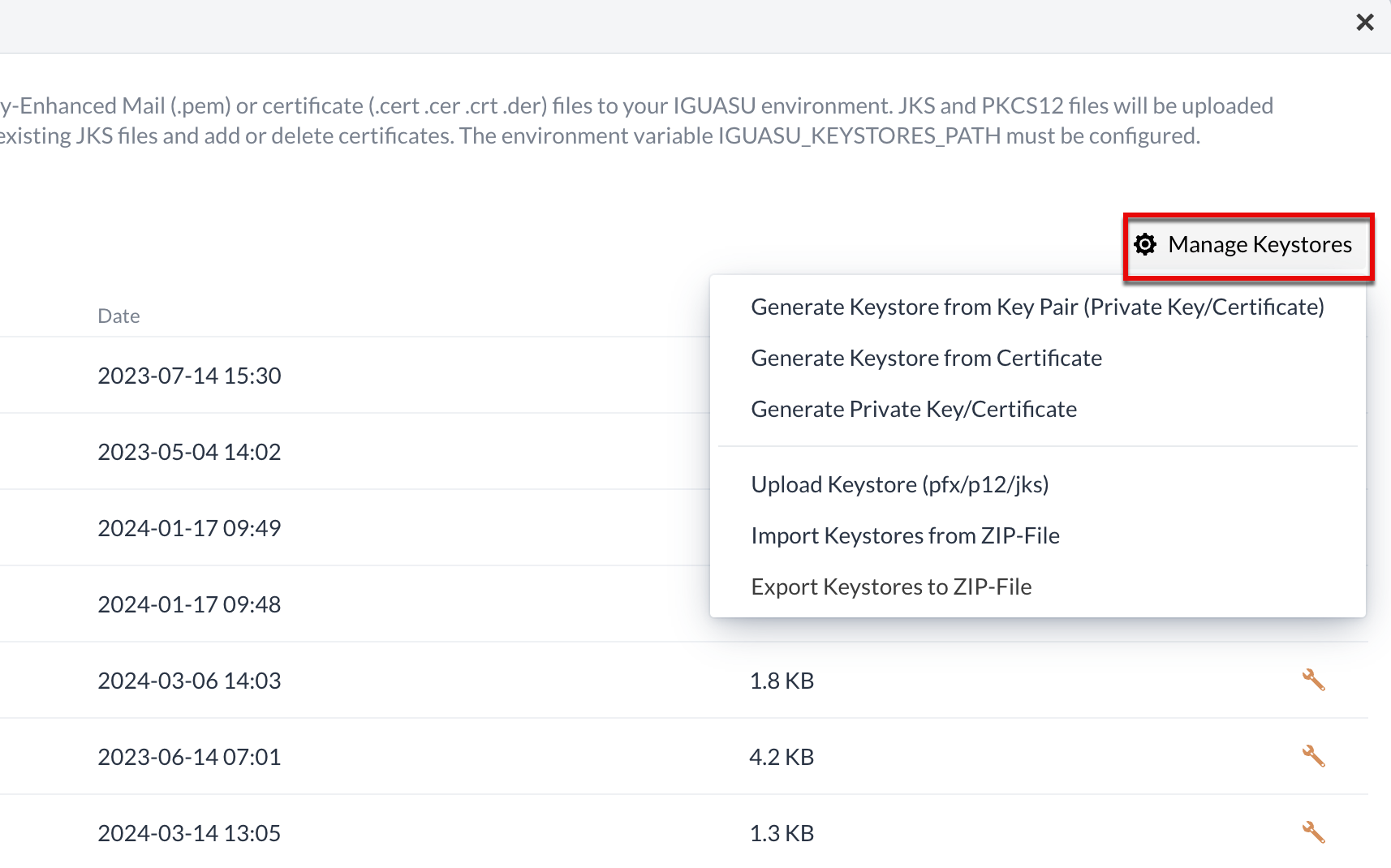
JKS, PKCS12 and PFX formats can be uploaded directly. All other formats are converted to JKS data before they are used.
In addition to the option to upload keystores, this view can also be used to generate a new keystore using either the appropriate keys or a certificate. Uploading this data is similar to uploading the keystores, where the selection opens another window in which the local data can be selected and added.
It is also possible to generate a new private key and the corresponding certificate via the certificate manager in IGUASU.
The option Generate Private Key / Certificate is selected for this purpose, which opens a new view.
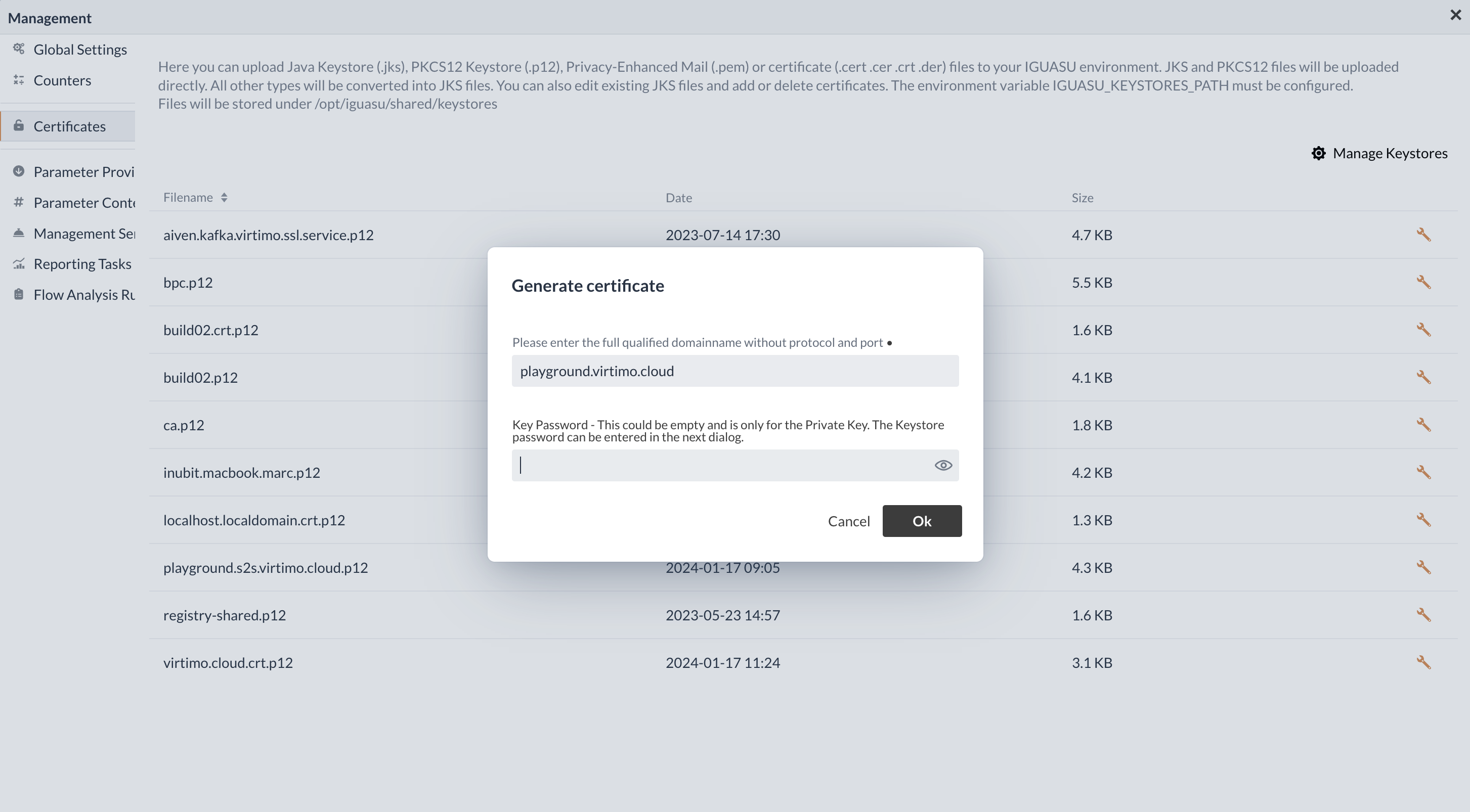
In this new view, the domain without the protocol and without a Port and a key password must be specified. Once both entries have been confirmed, a new window opens in which the keystore filename, the password and the certificate can be seen.
|
The password is not saved on the server. It should therefore be copied at this point and saved outside IGUASU. |
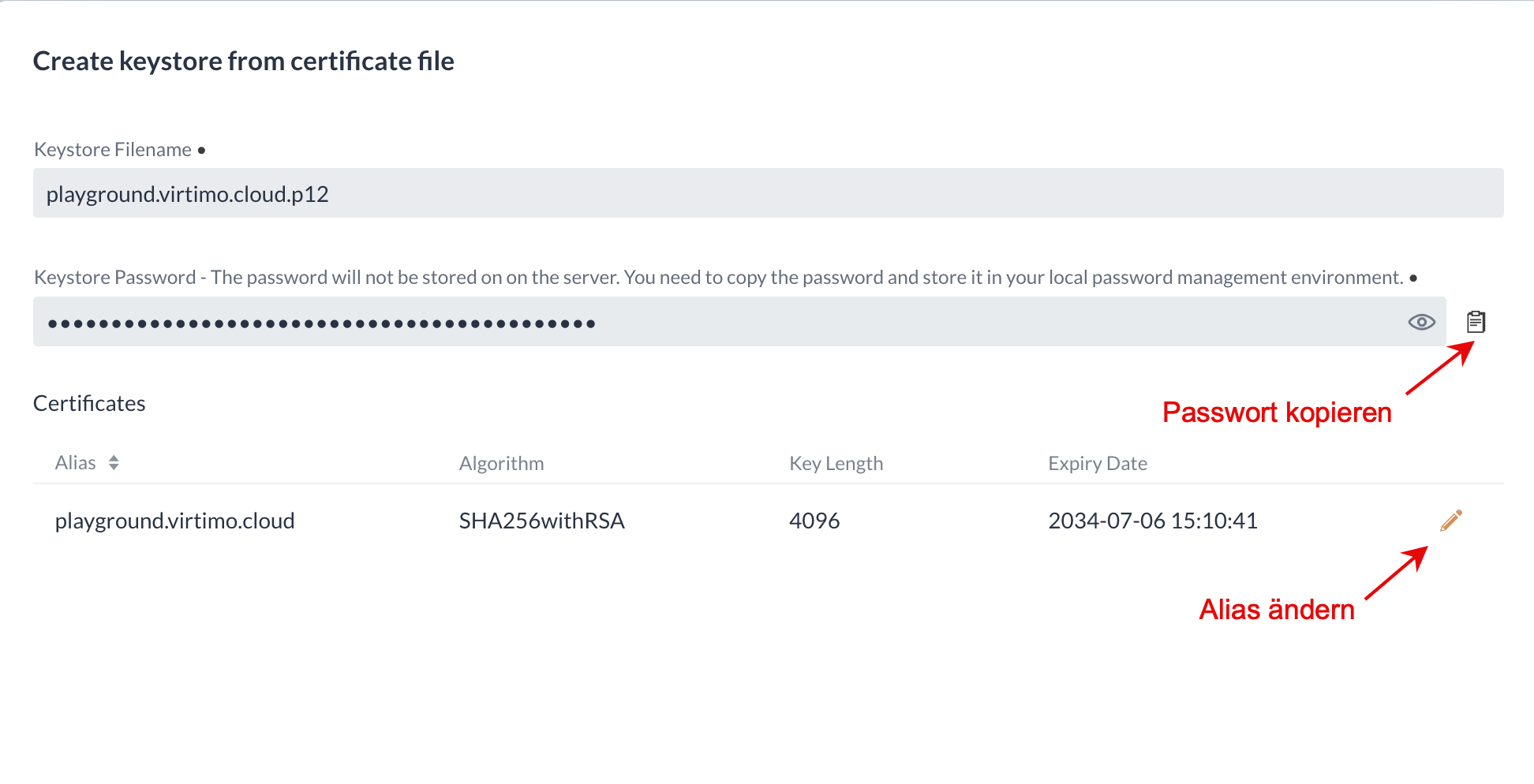
There is then an overview in which it is still possible to change the alias or copy the assigned password before the process is ended by saving.
Admin settings
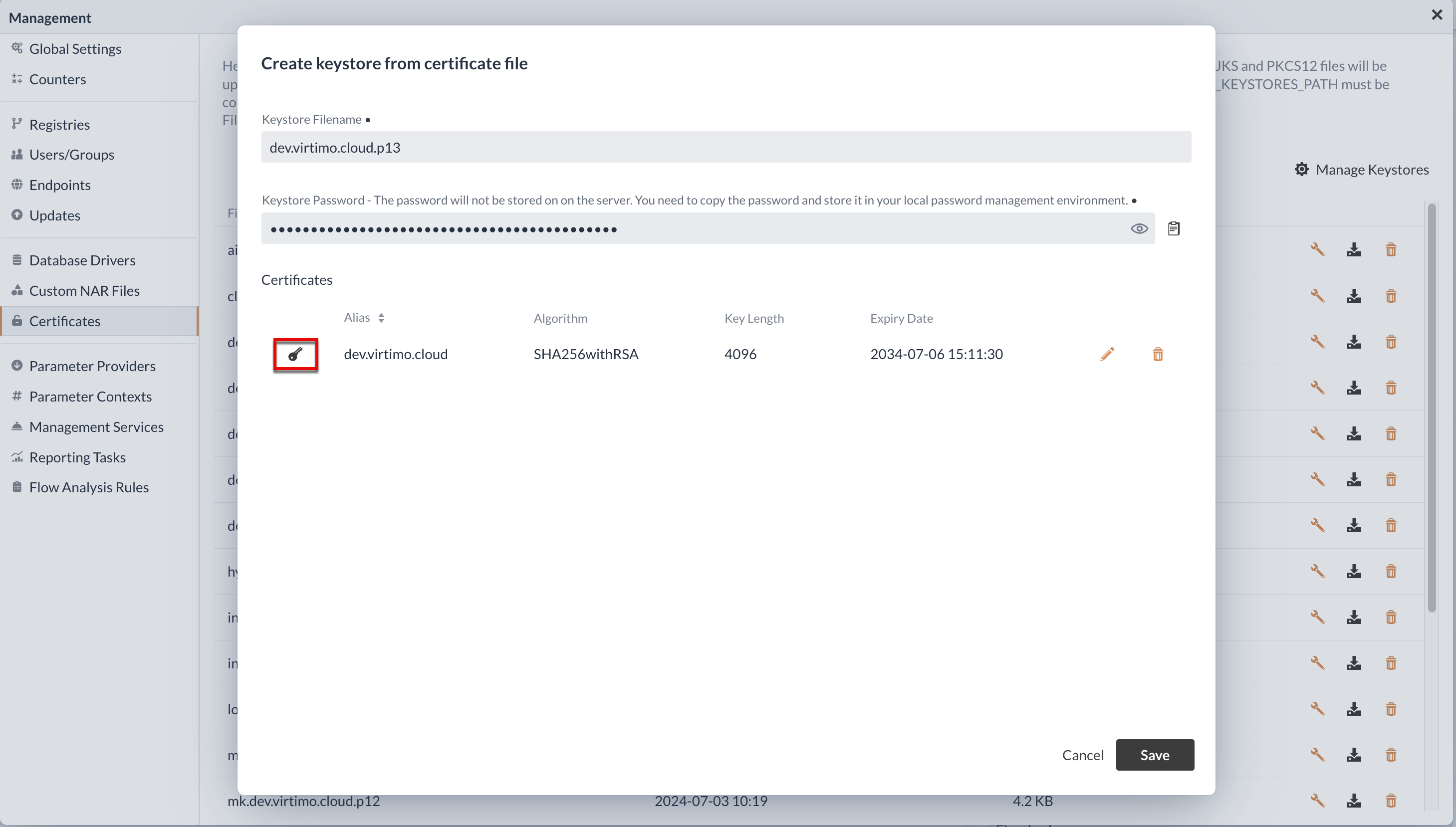
The key button next to the certificate can also be used to download the public and private key, which can be used for communication with other applications. It is also possible to adjust the alias or delete the certificate.
Existing keystores in the certificate manager can be adjusted after the corresponding password has been entered. It is also possible to download the keystores listed in the table. With these listed options, IGUASU offers various functions to customize the certificates and keystores in your own application and to use them for communication with other applications.
Parameter Providers
Properties of Processors, Process Groups and Services can be centrally configured and managed by using parameters. In this way, configurations can be outsourced. Parameter Providers enable the storage of parameters from sources outside IGUASU, such as AWS Secrets. The retrieved parameters of a provider can be queried by all referencing Parameter Contexts.
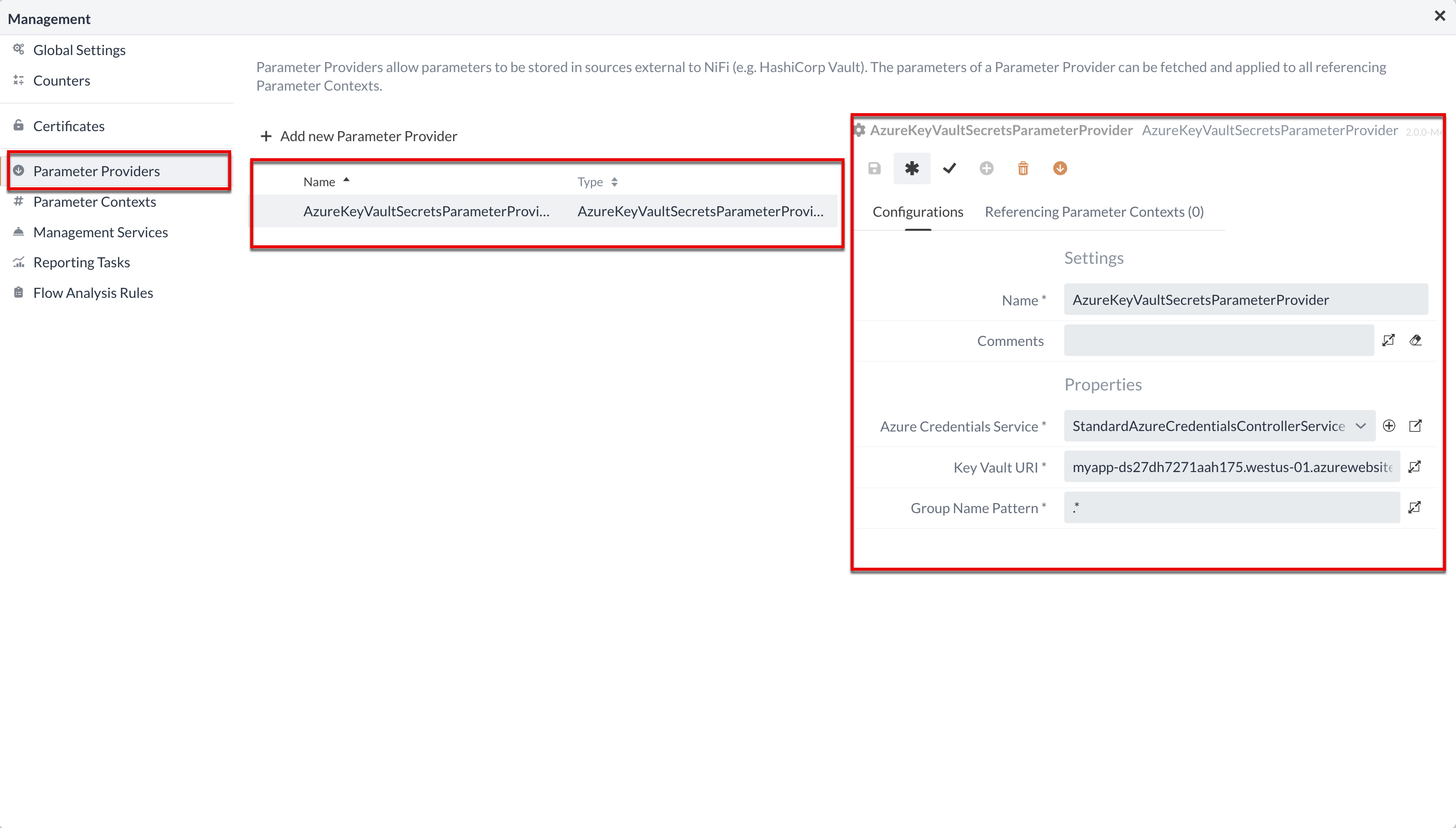
On the left-hand side of the Parameter Provider interface, there is a list of the existing Parameter Providers and their type. The right-hand side is used to define configurations for the selected Parameter Provider.
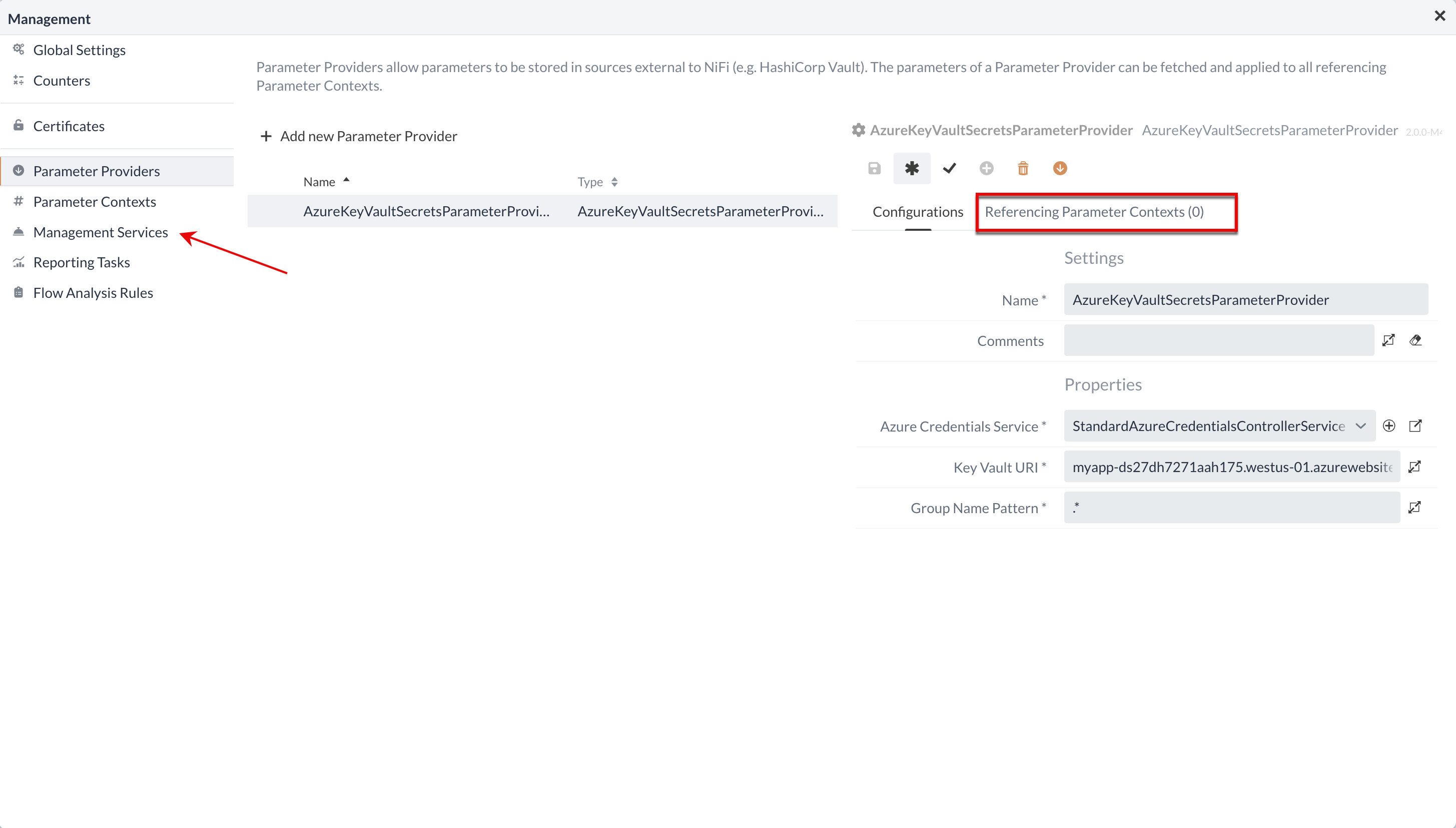
Parameter Providers are closely linked to Management Services.
The required Service must be activated after assignment so that the Parameter Provider can be actively used.
All Parameter Contexts that use the parameters of this provider are listed at Referencing Parameter Contexts.
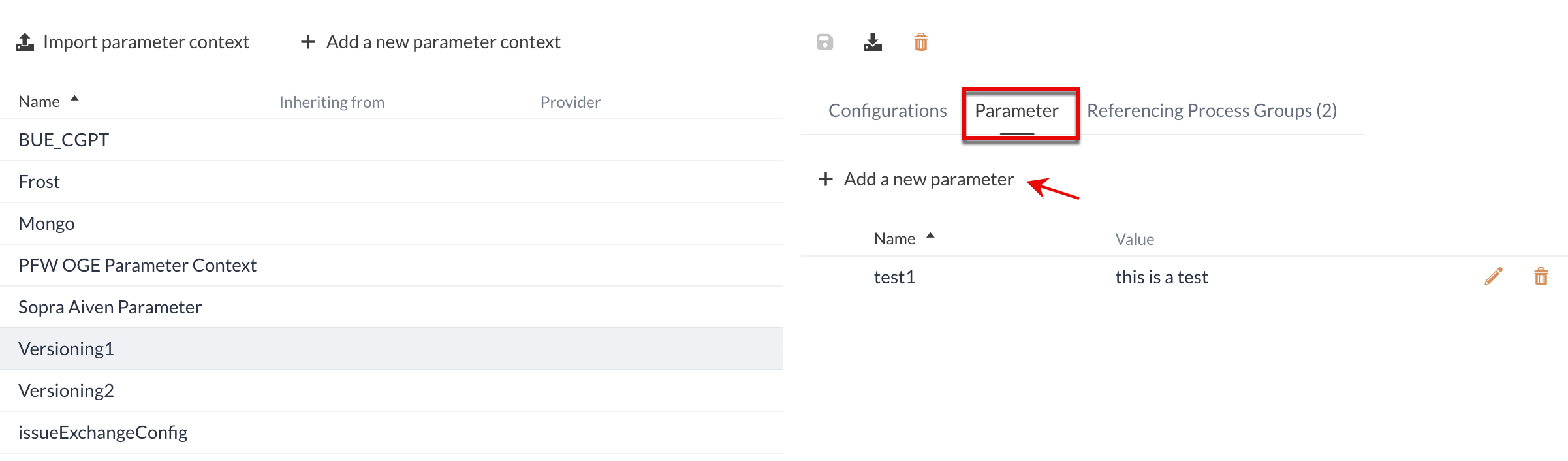
Parameter Contexts
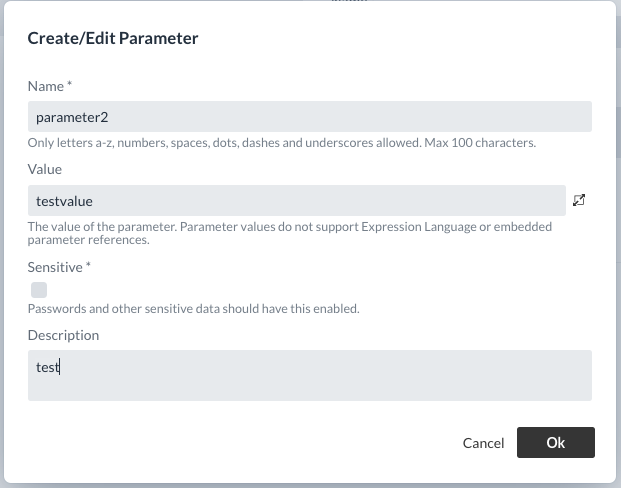
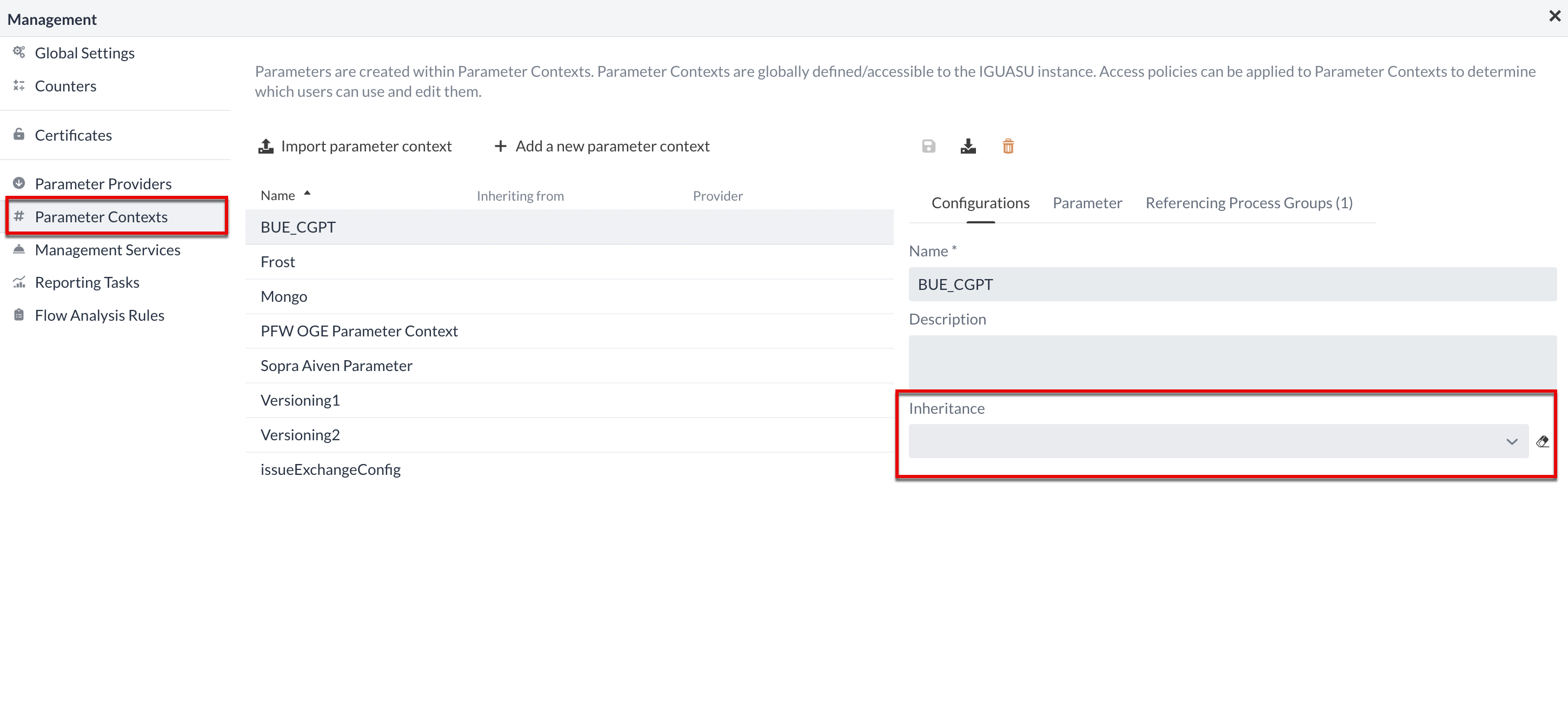
Parameters are managed by assigning them to a Parameter Context.
A Parameter Context can contain several parameters and receive parameters from one or more other contexts via inheritance(Inheritance).
In this way, configurations can be outsourced and exported or imported if necessary.
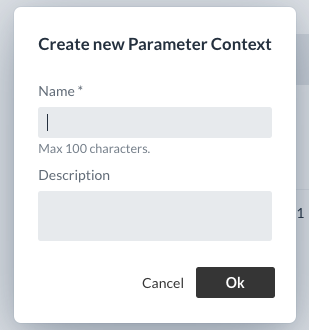
Create Parameter Context
A new Parameter Context is created via Add a new parameter context.
The name of the context must be unique.
After saving, the new context appears in the overview and can now be used.
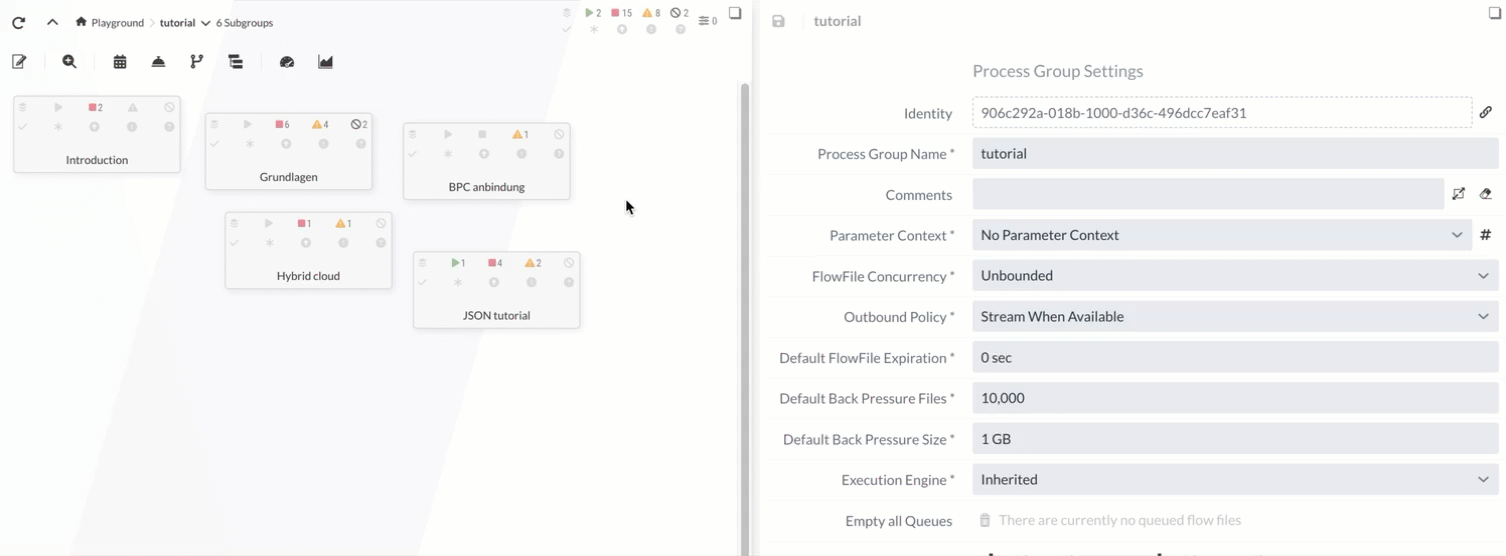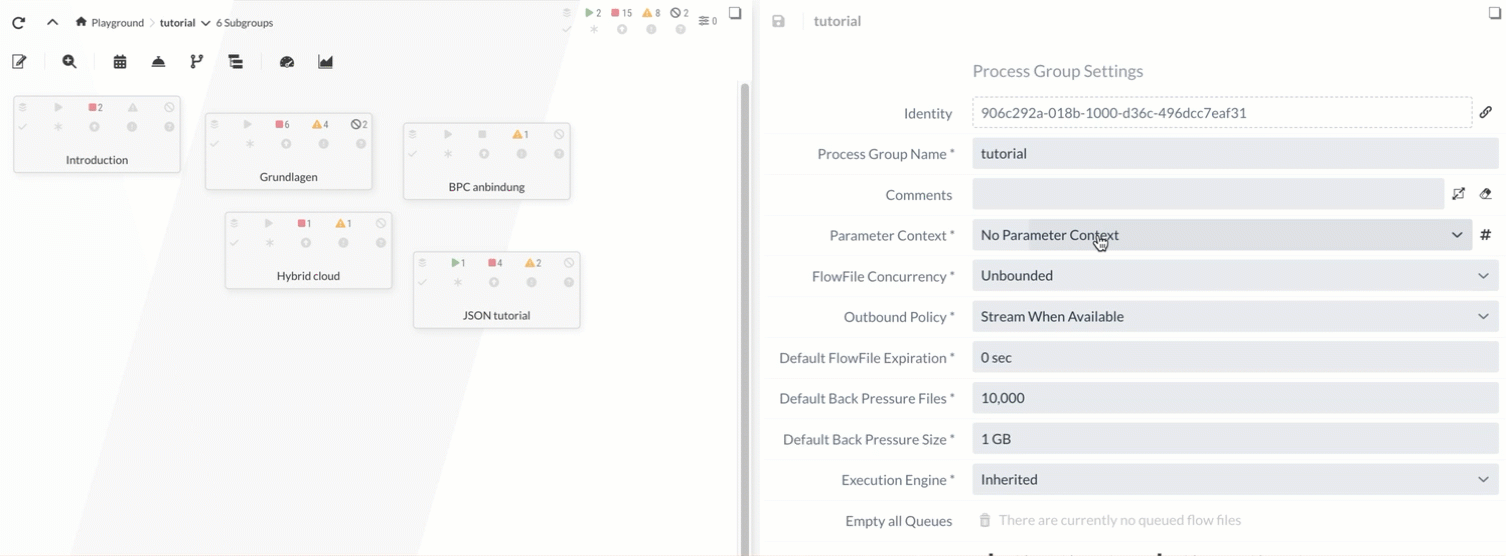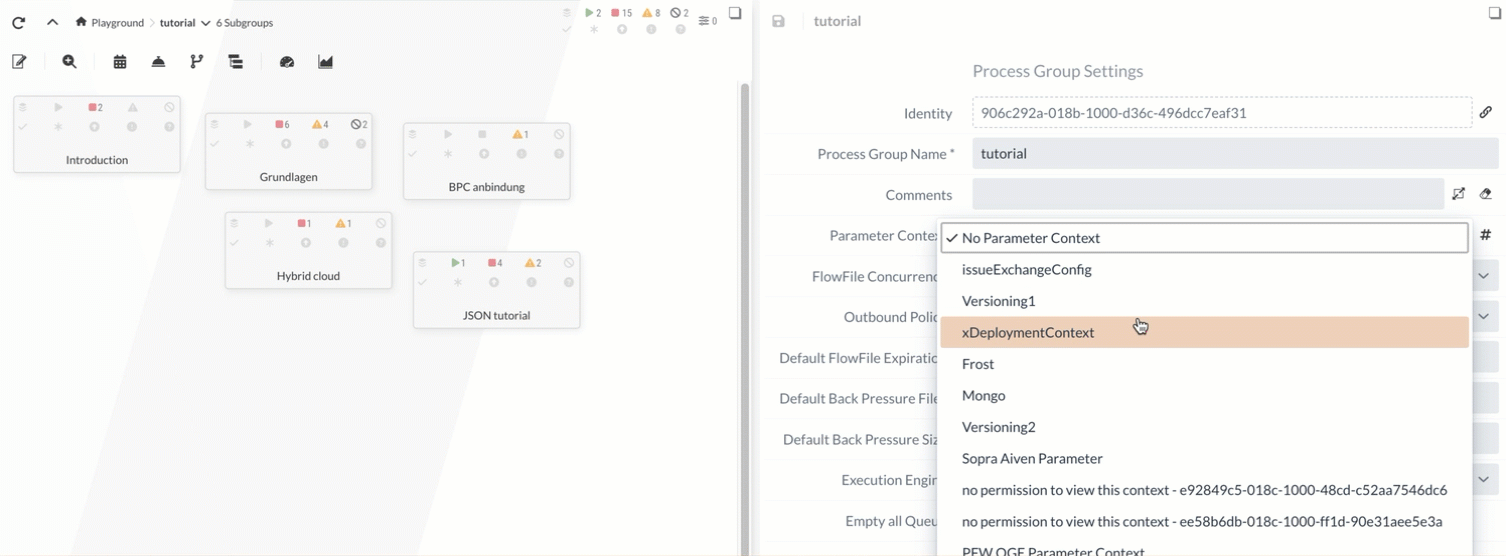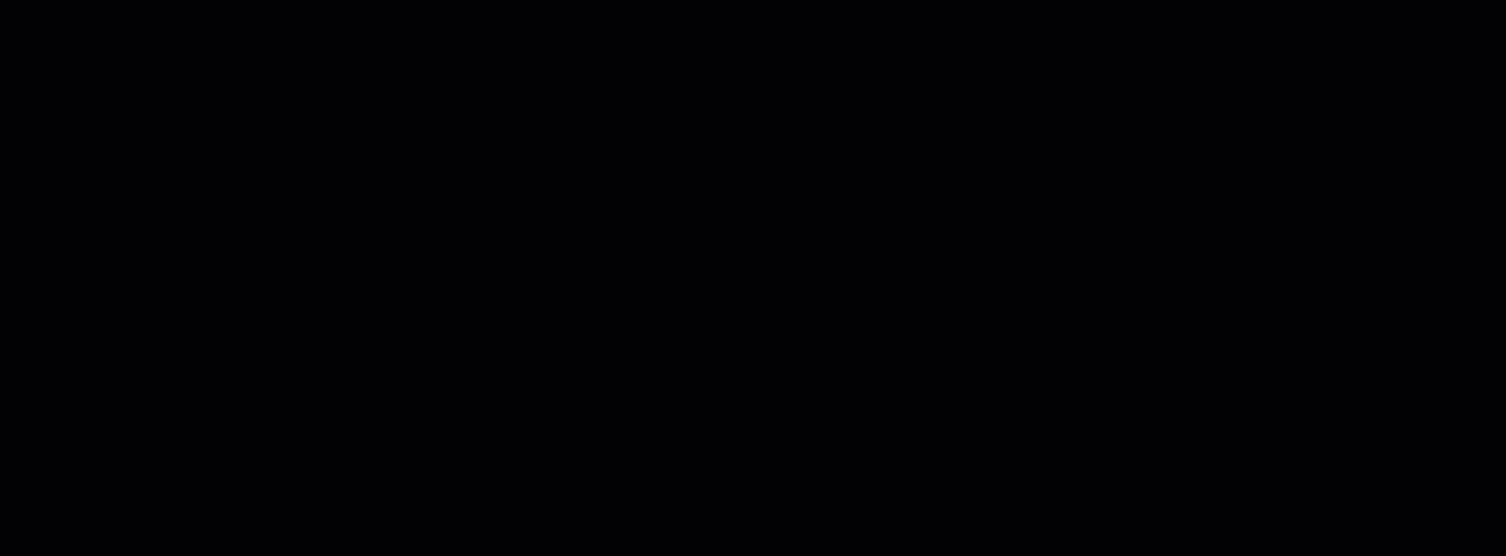
Assigning a context
The context can now be assigned to the Process Group in the Process Group Settings. The Parameters of this context are then available to all Services and Processors in this Process Group.
Using parameters
If a Parameter Contexts has been assigned to a Process Group, the parameter can be called up either by entering #{parametername} or by clicking on the 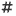 symbol next to the property of the selected Processor.
symbol next to the property of the selected Processor.
This works in selection boxes, checkboxes and text fields.
Parameters are evaluated directly after selection and the result of the evaluation is displayed.
You can also use the menu to:
-
Create a parameter from a property (if no parameter has been selected yet)
-
Jump directly to parameter management (if a parameter has already been selected)
-
Jump directly to parameter context management
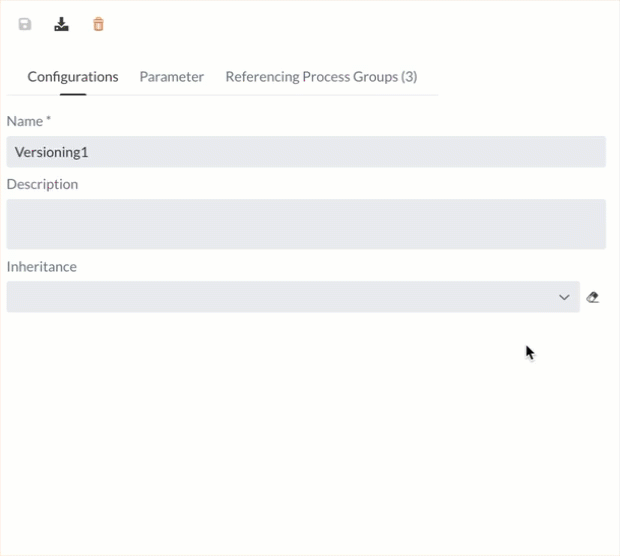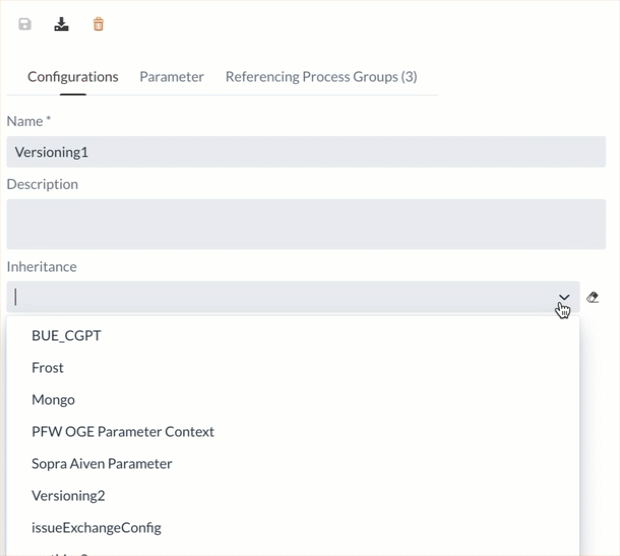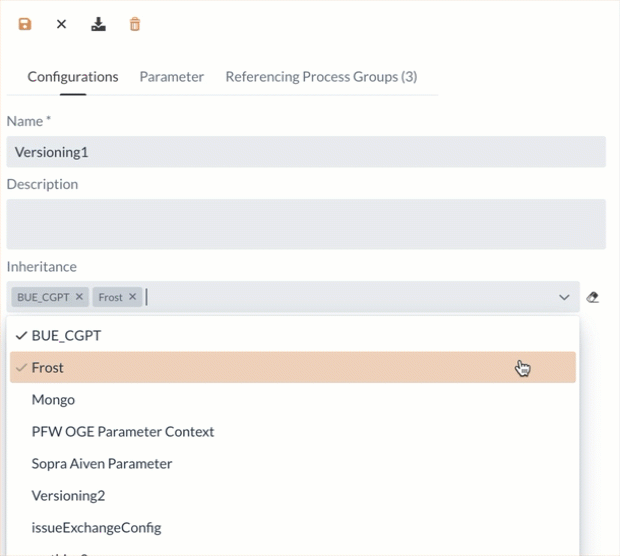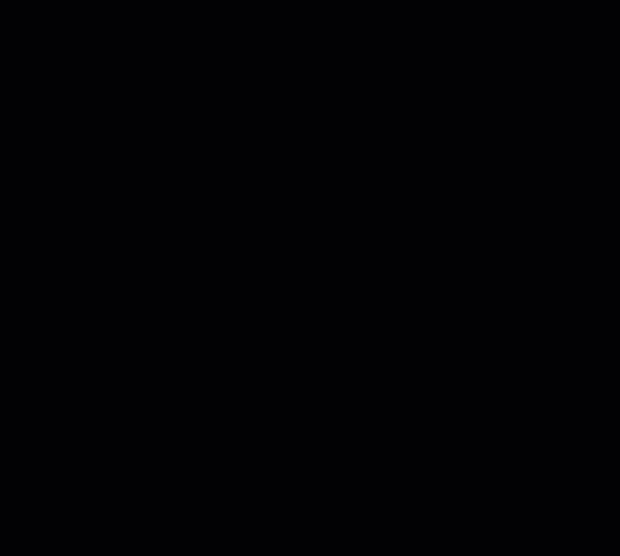
Inheritance of contexts
A Parameter Contexts can inherit parameters from one or more contexts. To do this, the desired contexts are selected in the drag-down menu. The deletion process is carried out for a single context by clicking on the cross. If you want to delete all selected contexts, you can click on the eraser icon.
The following order applies to parameters with the same name:
-
Parameters from the inheriting context overwrite inherited parameters
-
The order of inheritance: from top to bottom
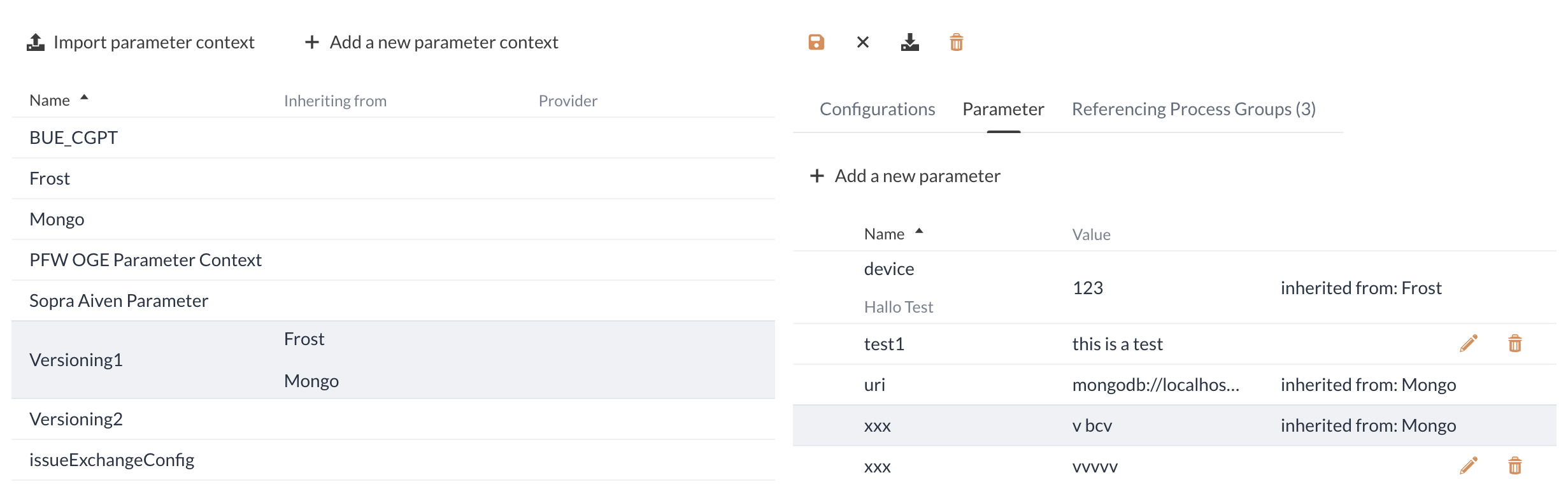
Inherited parameters cannot be changed or deleted within the inheriting context. Only self-generated parameters can be changed.
Export/Import of Parameter Contexts
Parameter Contexts can be downloaded individually using the download button.
They are imported again using Import parameter context.
If the context to be imported inherits from another context, this must be imported first, or a context with the same name must already exist.
Otherwise, the import is aborted with an error message.
Information that was previously marked as sensitive is not exported. In this case, the Parameters are exported without an associated value.
Download example as JSON: parametercontext.json
Management Services
Management Services are shared services that are ultimately not very different from Process Groups Services. These services can only be used by Parameter Providers and other services, such as Reporting Tasks, for configuration or task execution. These services cannot be used in Processors or other services at Process Group level.
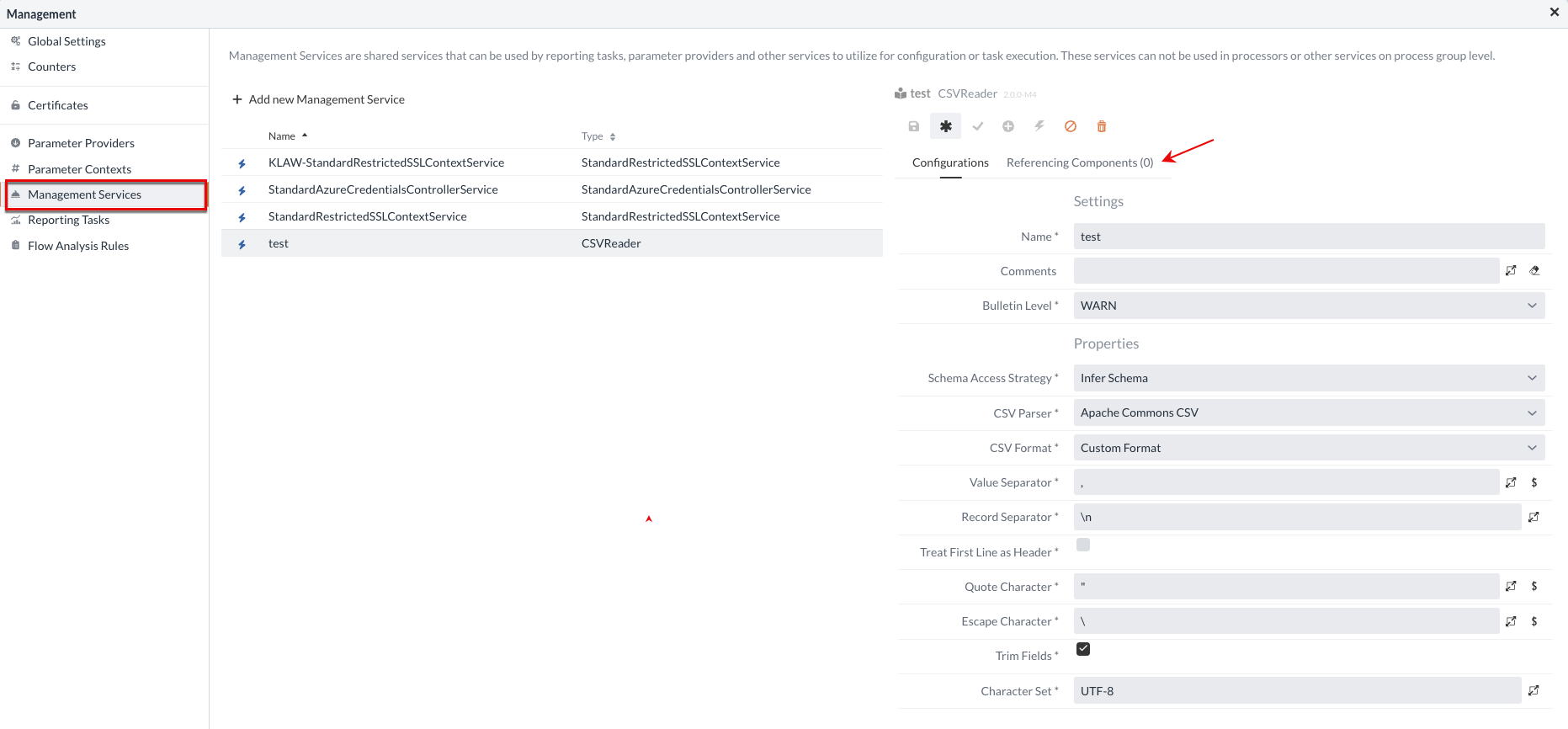
The Parameter Providers or other services that use this service are listed at Referencing Components.
Reporting Tasks
Reporting Tasks run in the background to create statistical reports on the processes in the IGUASU instance.
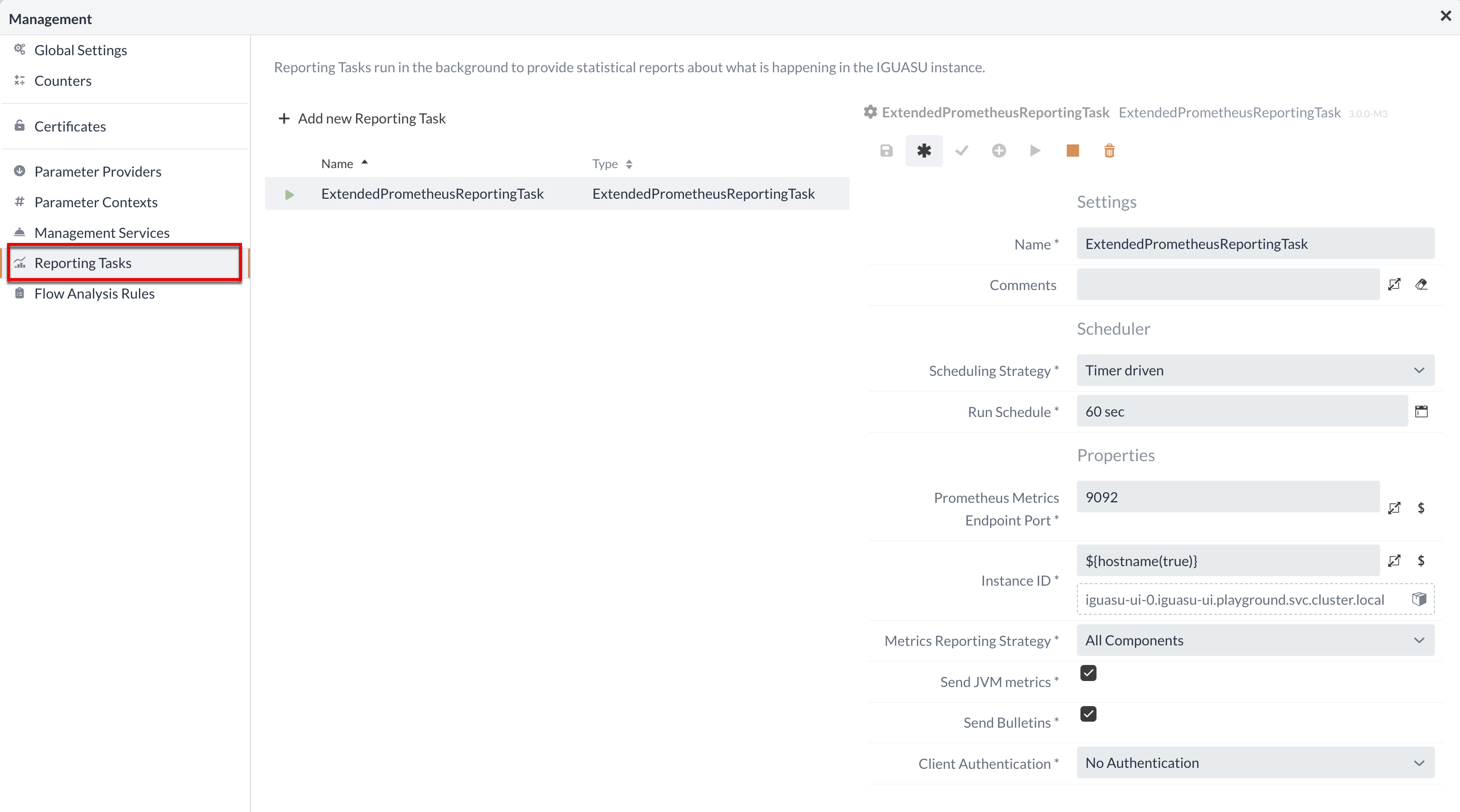
After the new component has been completed, it must be started explicitly using the Play button.
Flow Analysis Rules
Flow Analysis Rules can analyze components or (parts of) the diagram flow. They can lead to rule violations that can help to adjust or maintain an optimal flow design.
Under Flow Analysis Rules, restrictions can be set for users to exclude certain components or configurations when creating a flow.
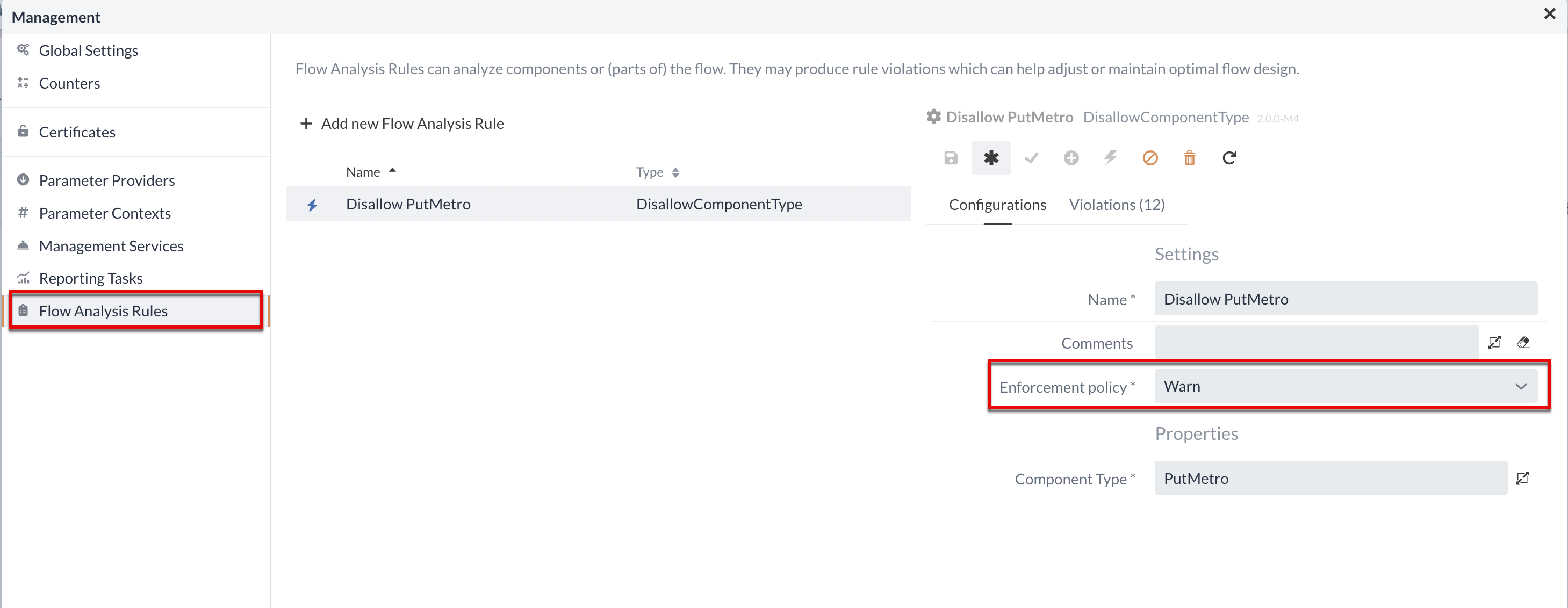
If, for example, a certain Processor should not be used, a Flow Analysis Rule can warn the corresponding users or exclude its use from the outset, depending on the default setting.
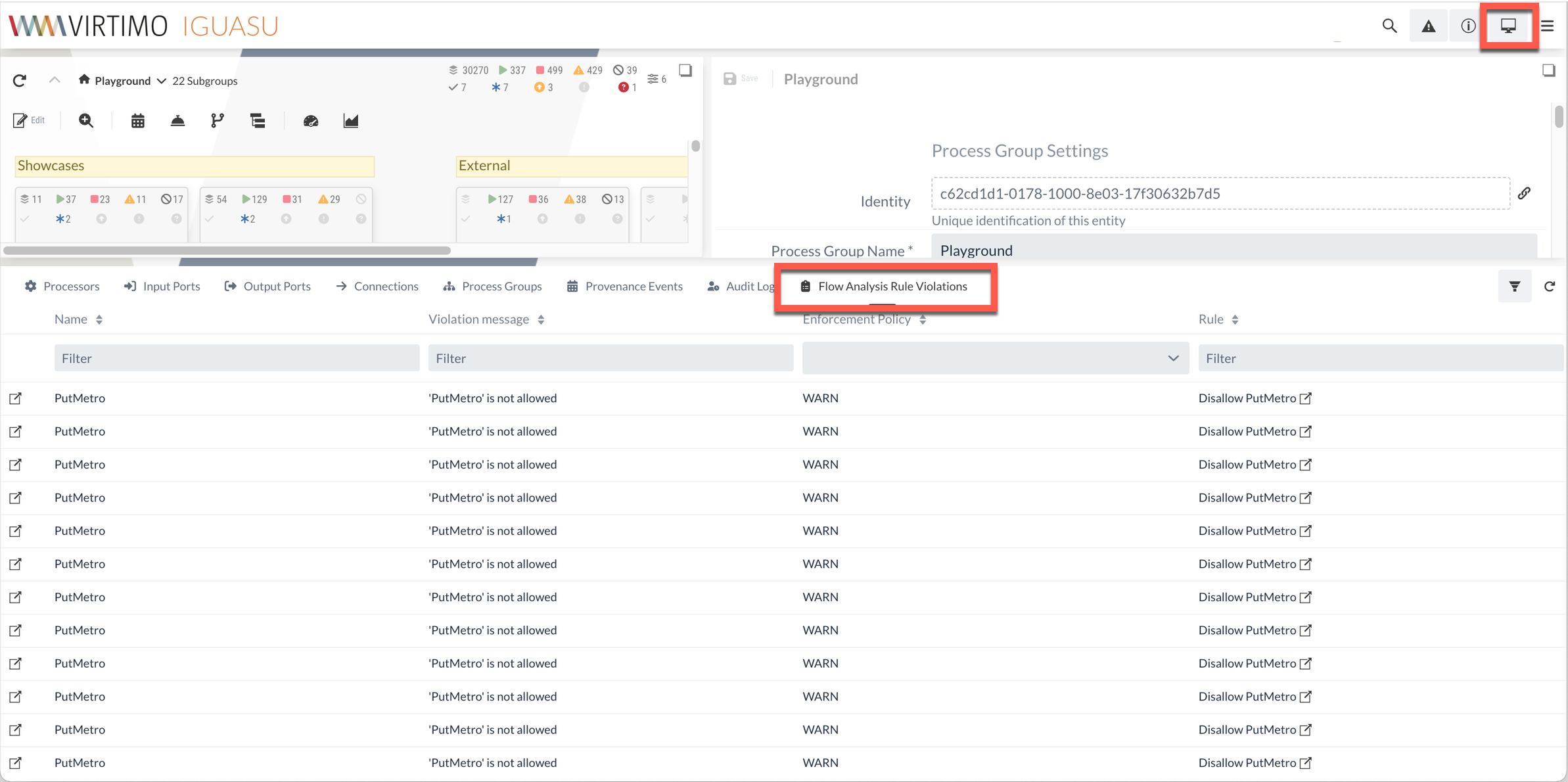
The Violations tab in the Management area provides an overview of the components that are currently violating the configured rule.
Alternatively, rule violations can also be monitored in the Monitoring view.
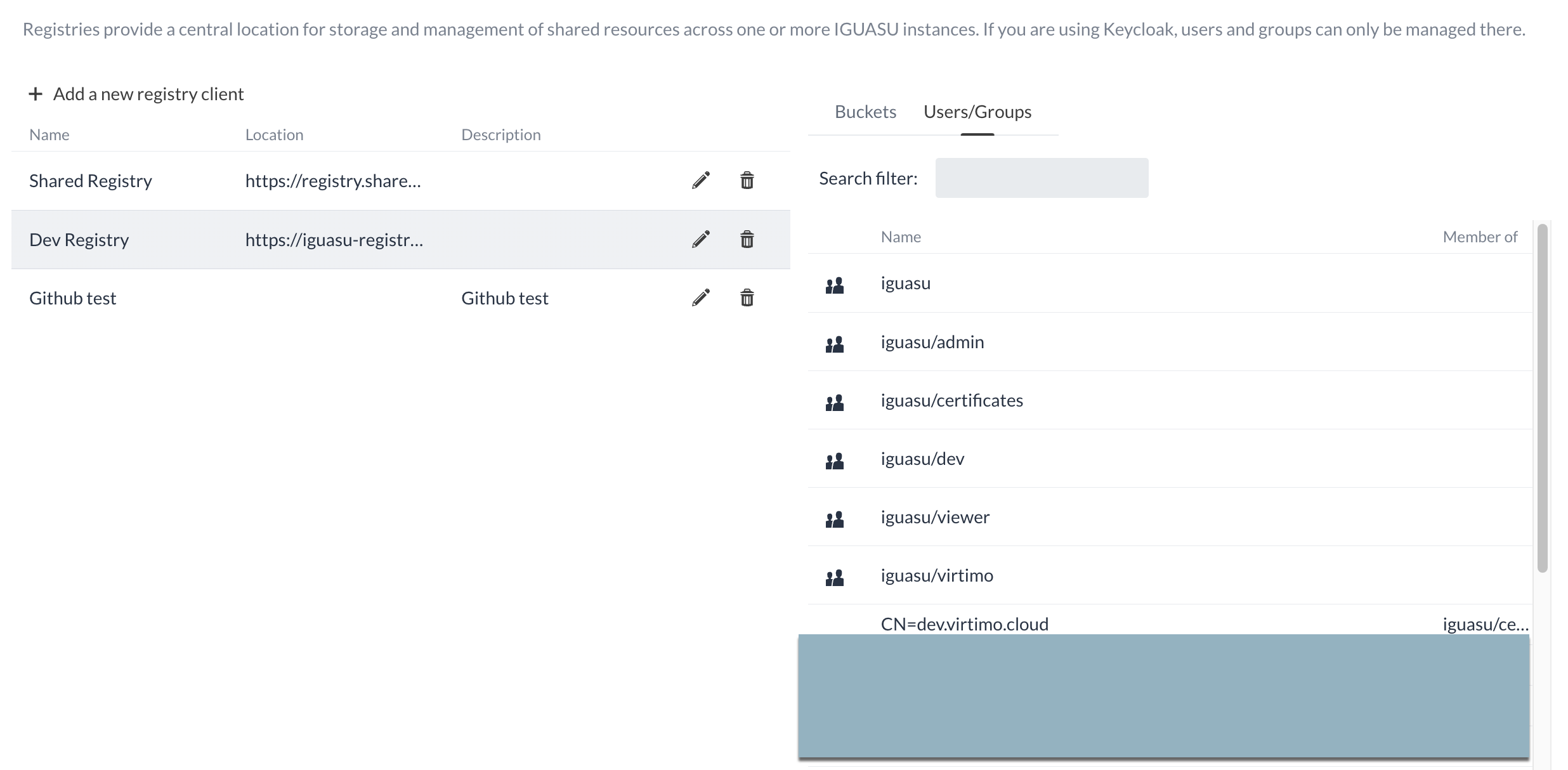
Registries
In the Registries section, registries can be configured that can be used for the reuse and versioning of configured Process Groups. A comprehensive description of the use of versioning in IGUASU can be found in the section Versioning.
Configuration of the registry
An IGUASU instance can optionally be connected to one or more registries. If this option is not selected, certain information related to versioning is not displayed in the User interface. The configuration takes place in the settings under the Registries item.
To open the settings of a registry, it must be clicked once. The only registry that cannot be configured in more detail is the 'Shared Registry', as this is shared.
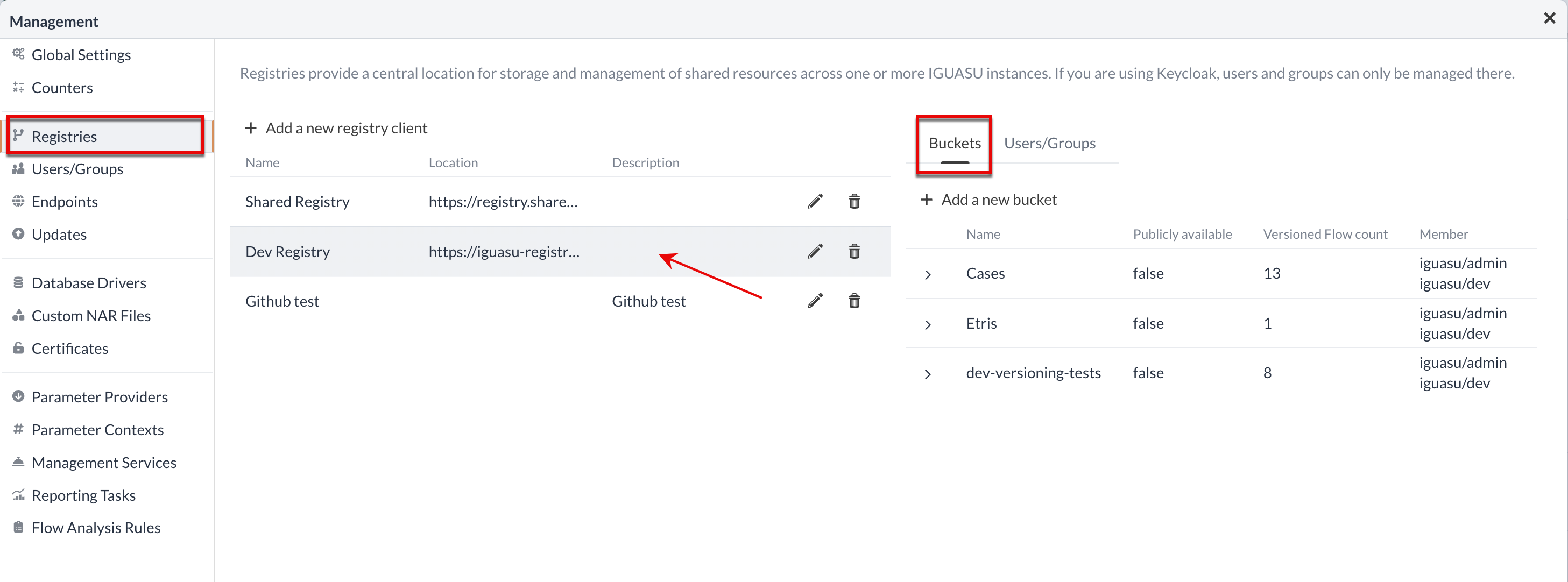
Any number of buckets can be created within a registry.
A bucket is a grouping of versioned flows to which different rights and therefore user groups can be assigned.
For this example, the checkbox Publicly available can be set so that the bucket is visible to all users.
Users/Groups
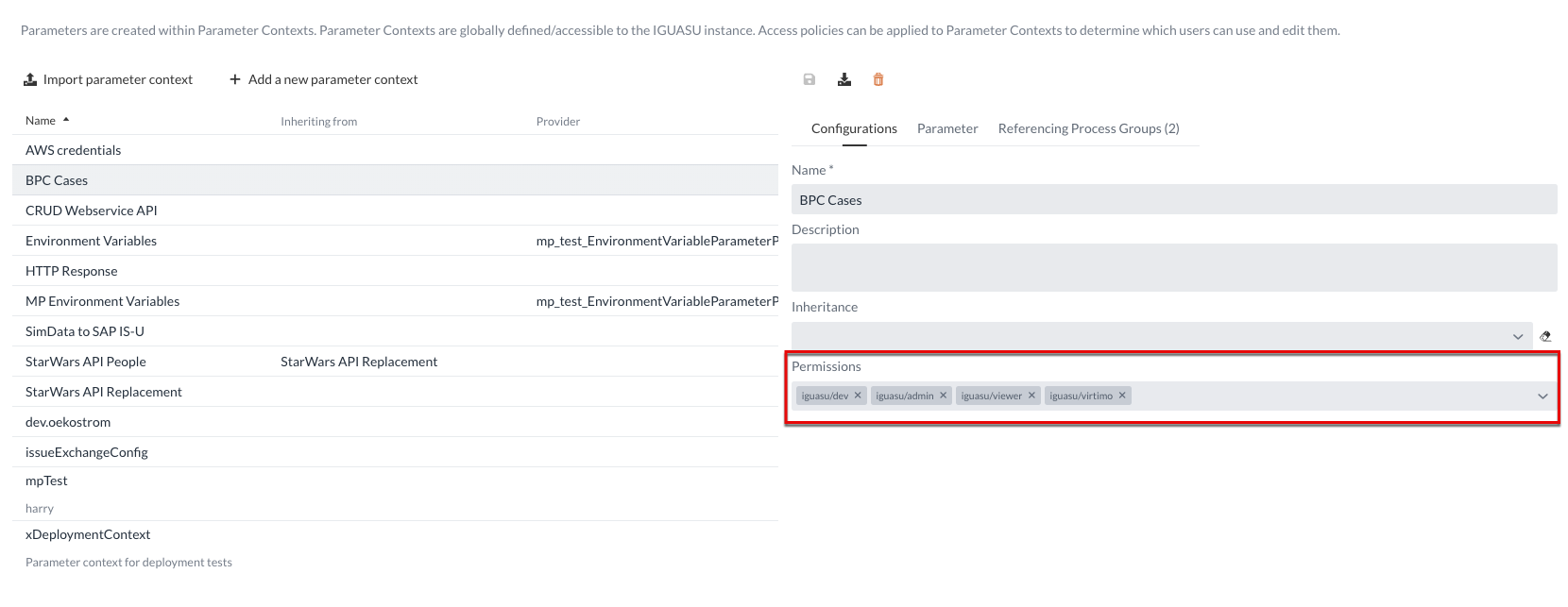
In the "Users and groups" section, the users and existing user groups can be viewed within the settings. The existing user groups as well as the registered users of the platform are displayed in tabular form in the menu. The identity provider Keycloak is used to manage the users and their groups.
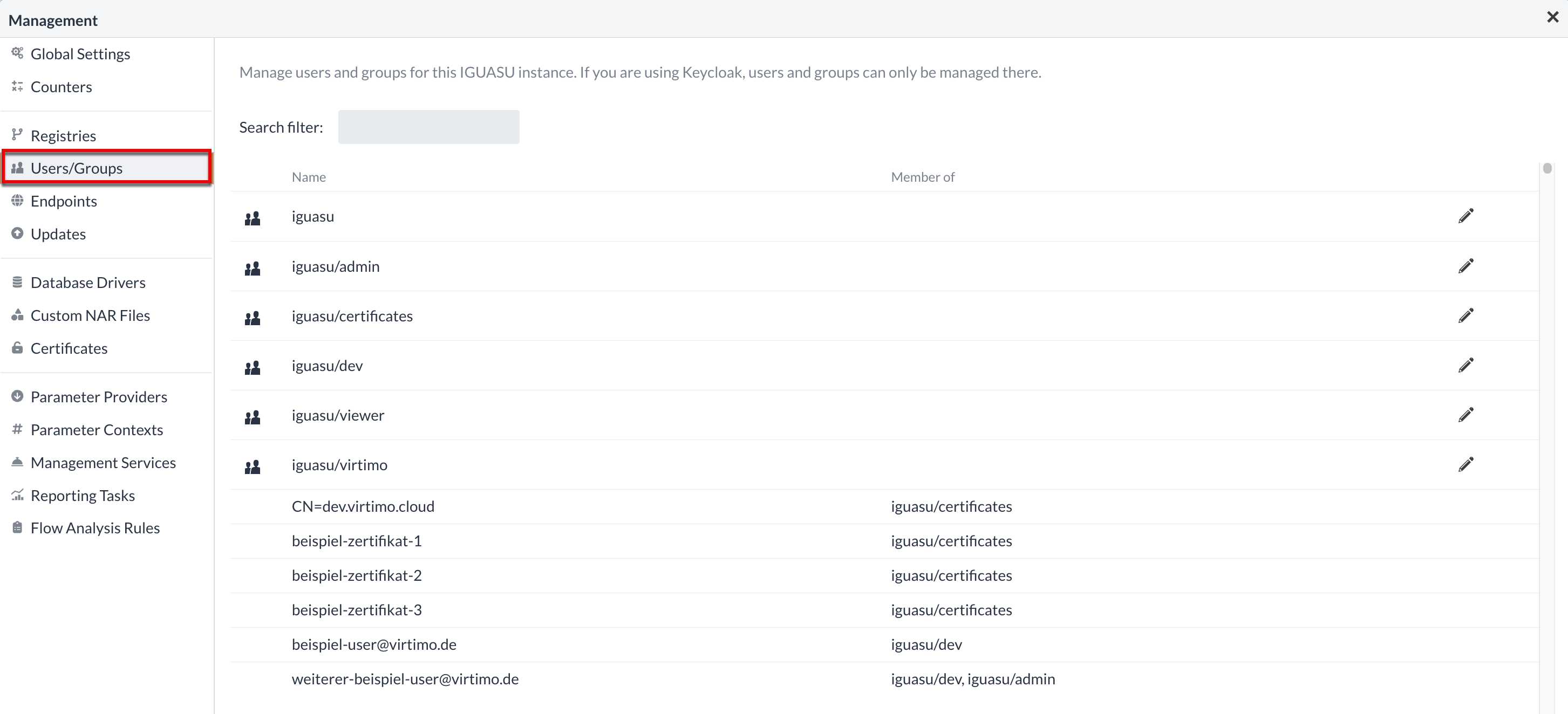
At the top of the table are the groups, which can be minimally adjusted by using the edit button on the right. In addition to the existing user groups, all users of the platform can also be viewed in the original table. The user groups in which these persons already exist are also listed.
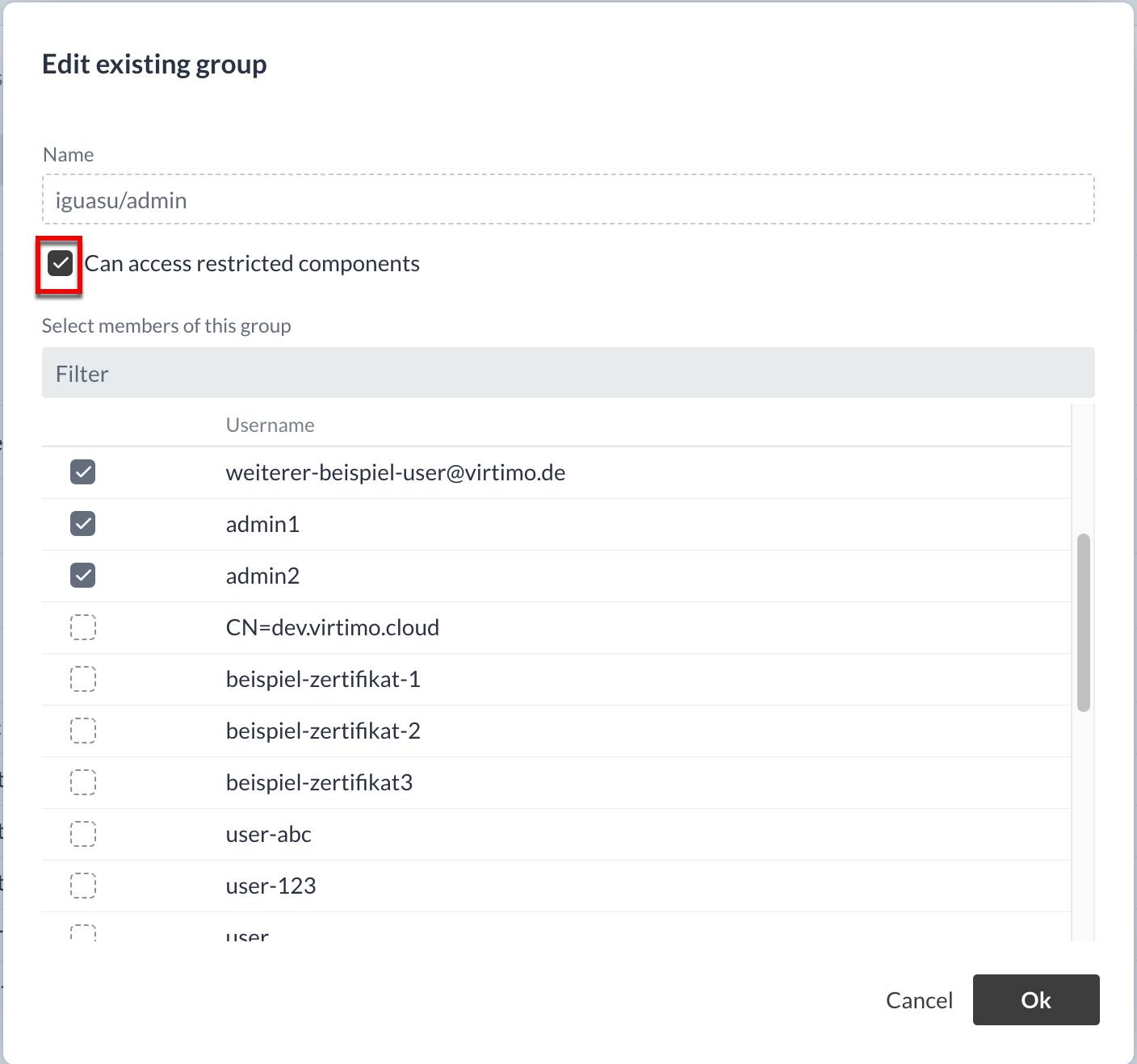
Clicking on the Edit button opens a new window in which the users are displayed.
Those who already belong to the group are shown by a selected checkbox.
The minimum customization in the group is ultimately the checkbox Can acess restricted components.
This means that every user in the group can now select restricted Processors.
|
User groups can be used to control the visibility of Process Groups in the Diagram. In Configuration area of the corresponding Process Groups, you can define which user groups the Process Group should be visible to. |
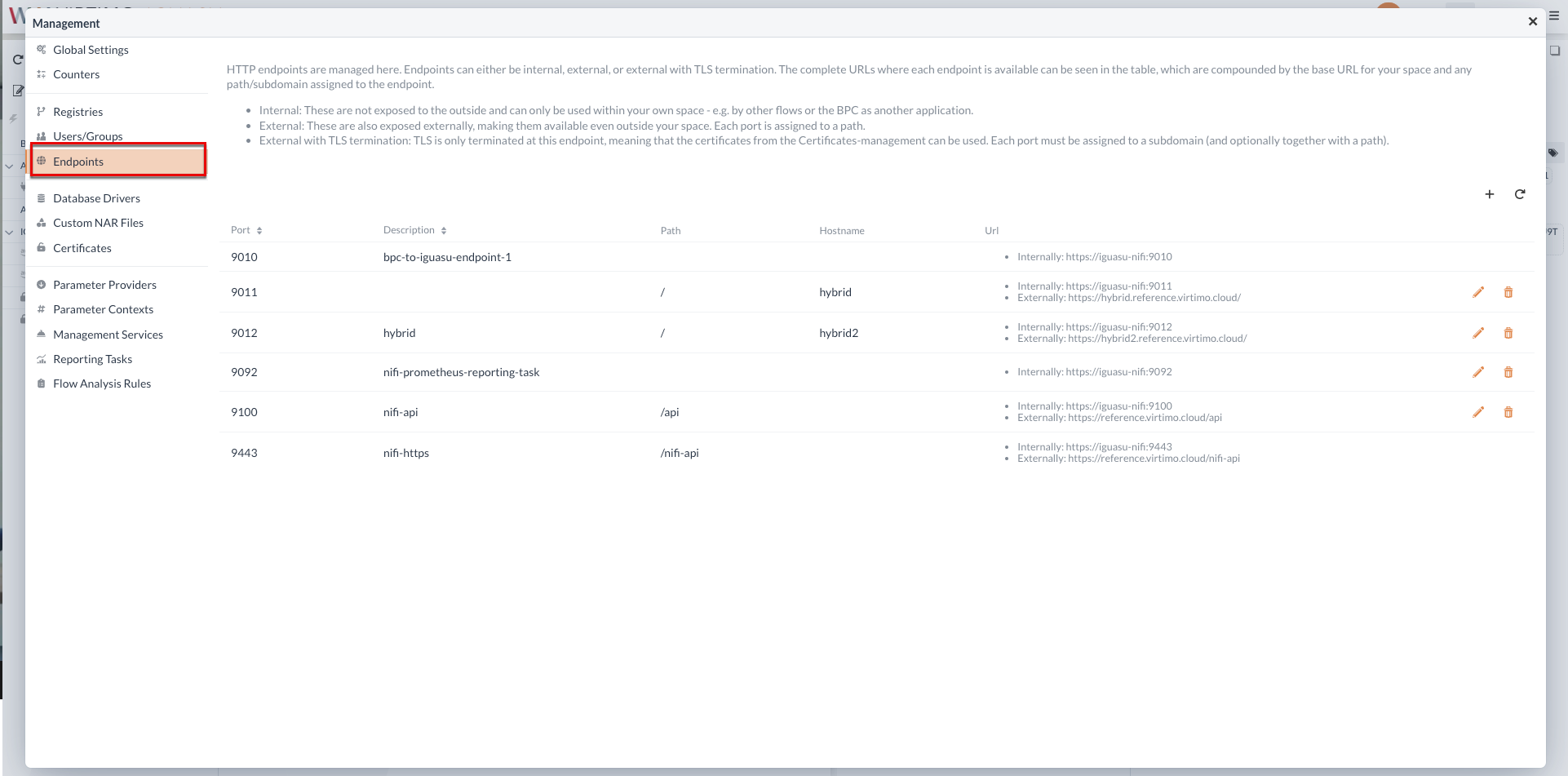
Endpoints
HTTP endpoints can be managed here. Endpoints can either be of the type Internal, External, or External with TLS Termination.
Internal: Internal endpoints can only be reached within their own namespace (e.g. by other flows or the BPC) and cannot be used from outside. Internal Ports are addressed by the Service name https://iguasu-nifi:<port>.
External: External endpoints are publicly available and should be secured accordingly. The call is made via https://<domain>/<path> and is then forwarded to https://iguasu-nifi:<port>.
External with TLS Termination: In contrast to the External type, TLS is terminated directly at the endpoint and not at the HTTP proxy in front of it. This is required to be able to use TLS.
It is necessary to create a subdomain for this.
The call is made via https://<subdomain>.<domain>/<path> and is then forwarded to https://iguasu-nifi:<port>.
Endpoints that cannot be changed or deleted belong to the standard endpoints that are necessary for the operation of the application.
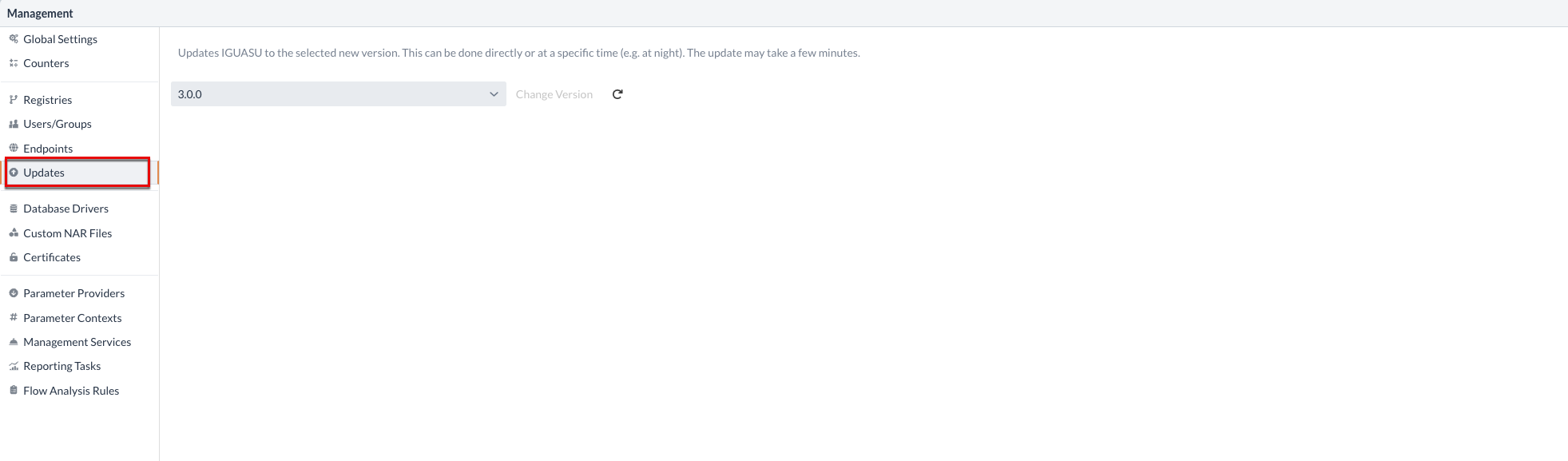
Updates
Under the "Updates" tab, IGUASU can be updated to the selected new version.
This can be done directly or at a specific time (e.g. at night).
The update can take a few minutes.
After clicking on the Change Version option, the update process is triggered.
Database Drivers
In this view, JDBC drivers can be adapted or uploaded in IGUASU to enable the connection to databases. Existing drivers are listed in tabular form, with the file name and when they were added.
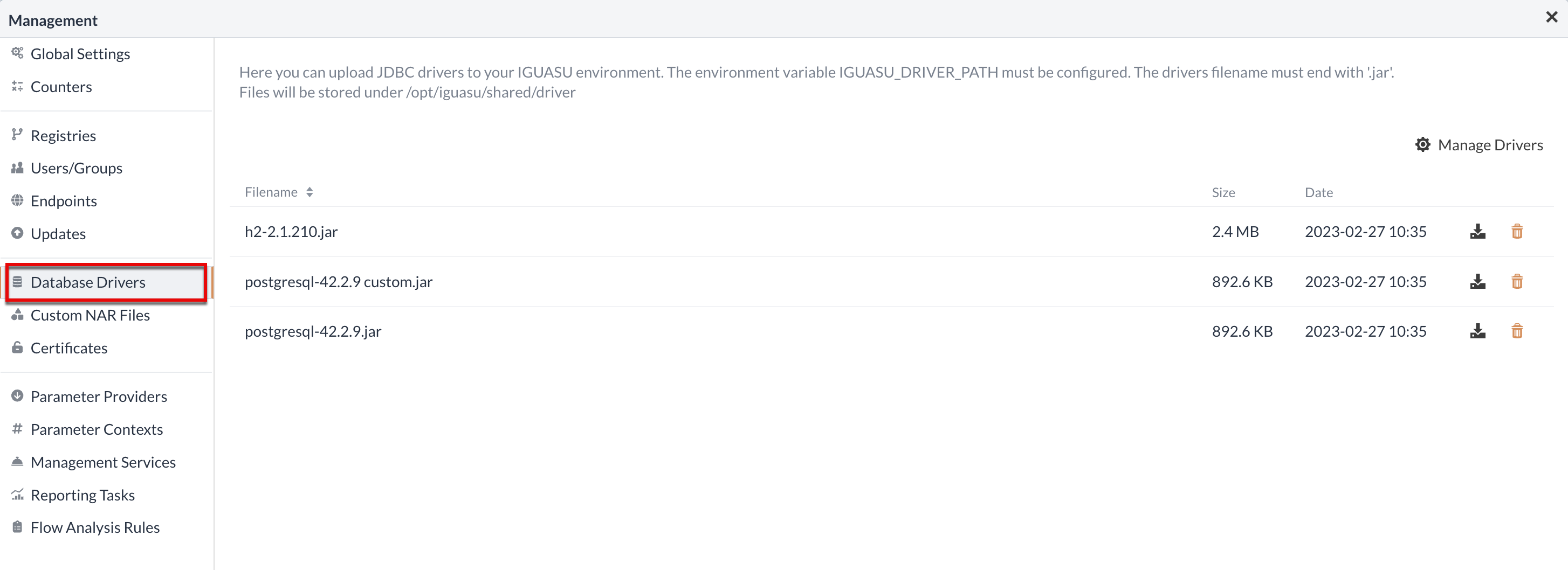
When uploading drivers, it is important that the file names have the extension .jar in order to be used in the system.
Uploaded drivers are saved at opt/iguasu/shared/driver.